Enable Teams to Fix The Risk They Own
Route data security issues to the right owners with clear instructions to remediate issues directly.


























































Break Silos.
Drive Accountability
Make data security findings accessible to a wider range of employees and strengthen your data security culture org-wide.
Drive accountability. Mitigate Risk
Reduce data breach likelihood by empowering employees to review and act on risks associated with unauthorized access or misuse.
Make Informed Decisions Responsibly
Force-multiply data security by sending notifications directly to data owners, including issue explanation and steps to remediate.
Strengthen Data Security Posture
Implement robust security measures, establish clear governance policies, and track completion rates of issues mitigated by data owners.
Make Data Security
a Team Effort
Empower employees from across the business to understand and act on data security risks that they are responsible for. Simplify the process and lower time commitments via specific notifications and an dedicated and actionable remediation portal.
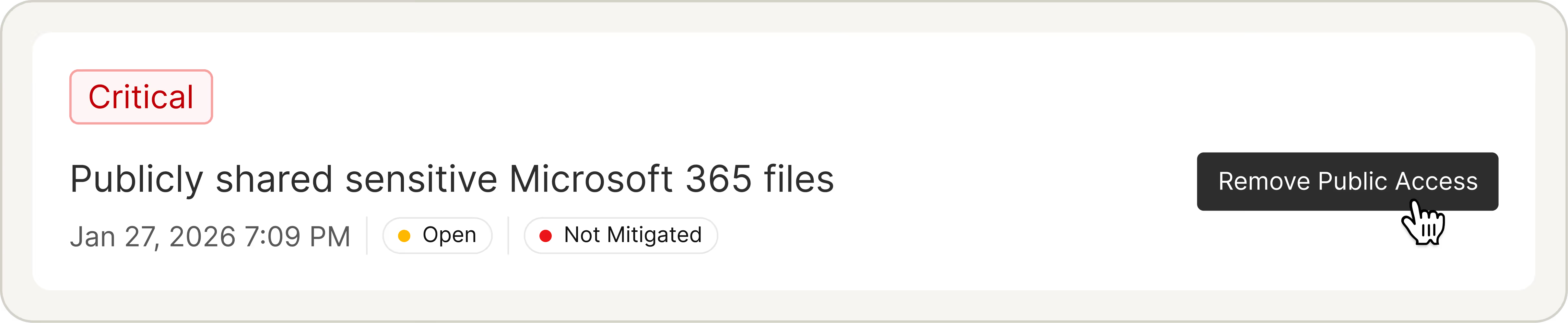
Put Fixes in the Hands of Data Owners
Reduce remediation time by routing actionable notifications to data owners via email, Slack, and Teams. Enable fast resolution with specific context and instructions. Close the loop in a dedicated portal that is easy-to-use and auditable.
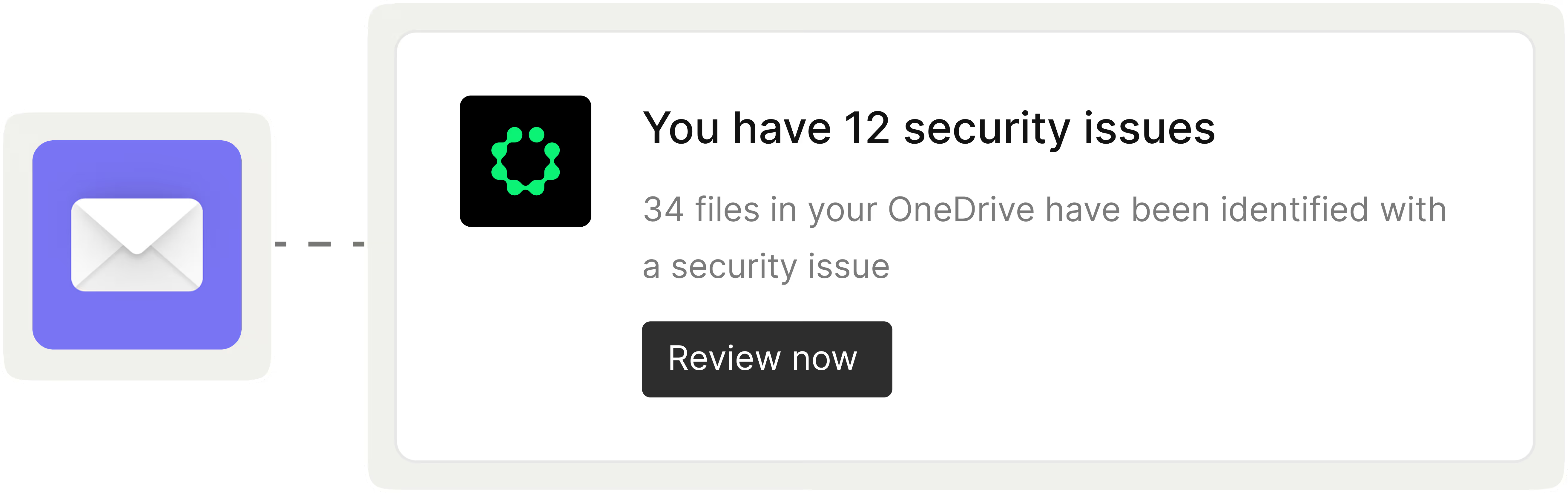
Take the Right Action at the Right Time
Make risk clear to non-security teams so they can focus on what matters most with the automatic deprioritization of issues that are no longer relevant or low-risk and updated urgency and impact of an issue in real time.
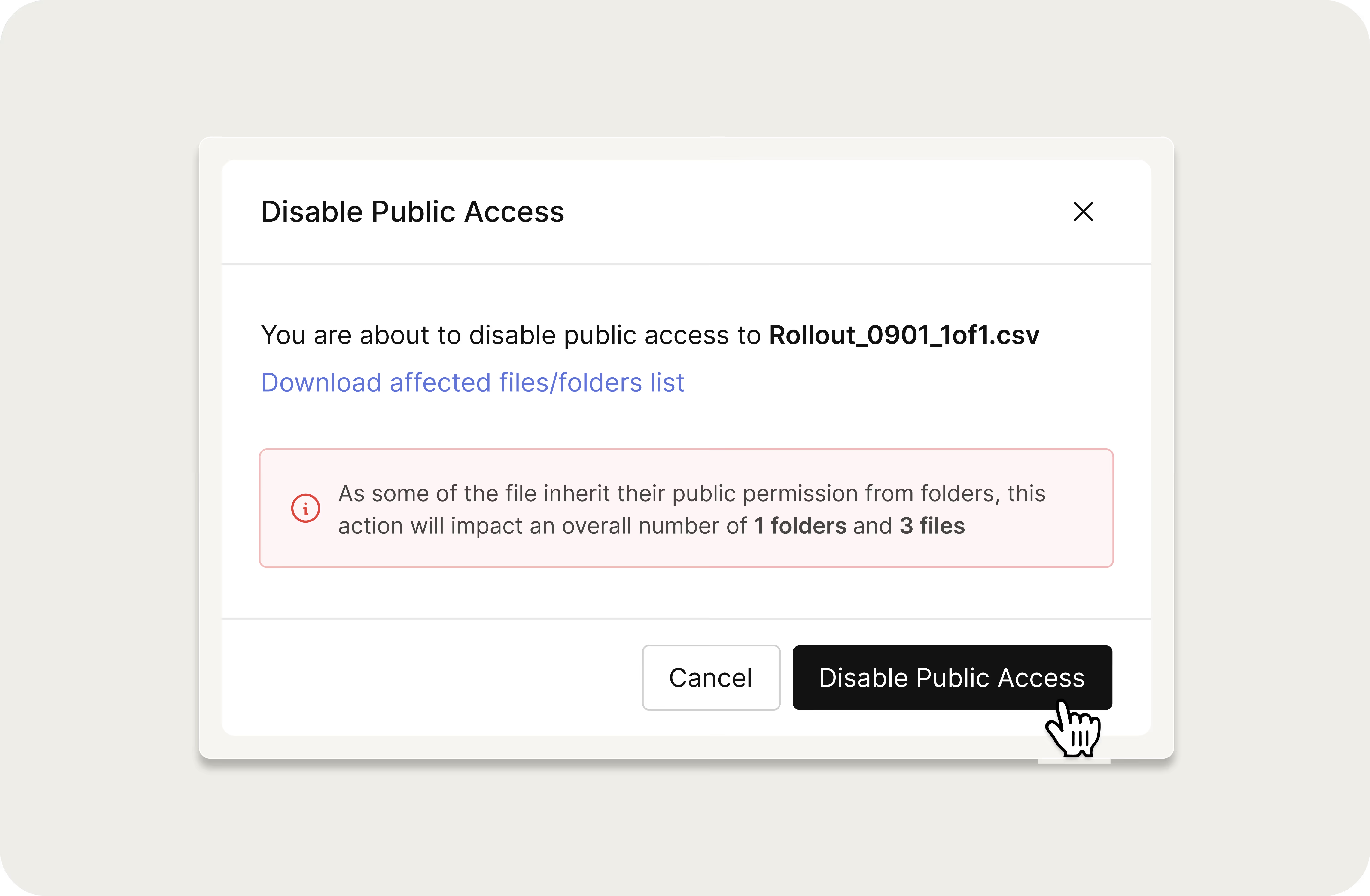
Delegate Risk Management
Empower business unit owners to manage their own data risk with the ability to triage issues, remediate, track outcomes, and fix health issues.
FAQs
Cyera’s remediation actions fall into two categories - Notifications and Active Remediation. Notification actions ensure the right people are alerted and empowered to act quickly. They allow internal stakeholders, such as remediation teams or datastore owners, to participate directly in the remediation process, thus reducing effort by putting data risk remediation in the hands of those. Active Remediation actions allow you to take direct action through the Cyera platform without involving additional stakeholders in the process. These actions apply to different entities. Some apply to the datastores (such as removing public access from an S3 bucket), others apply to objects and additional ones may apply to identities.
Key capabilities include manual and automated workflows that trigger targeted alerts via email, Slack, Microsoft Teams, and Jira, leading to guided response and democratized remediation.
Datastore-level actions, Object-level actions, and Identity-level actions. A few examples include removing public or org-wide access, applying sensitivity labels, and reduce excessive permissions.
Yes, with Send issues in a Slack message, you can notify data owners about security issues directly in Slack. By integrating with Slack, Cyera helps democratize remediation across your organization, ensuring issues are seen and acted on faster, without relying solely on email.
Yes, beyond Cyera’s out-of-the-box actions, you can create webhook-based custom remediation actions tailored to your environment.


.svg)