Discover and Protect Your On-Prem Data
Discover, classify, and secure on-prem data with Cyera’s AI-native data security solution, built for unprecedented speed, scale, and precision.
























































































Unified Data Security Across All Environments
Secure data across on-prem, SaaS, DBaaS, and IaaS environments with a single AI-powered platform.
Automated Discovery and Classification at Scale
Deploy quickly and gain immediate visibility into sensitive on-prem data, including files, databases, and application data, with 95%+ classification precision at petabyte scale.
Complete Visibility for Confident Compliance
Automatically surface high-risk sensitive data stored on-premises and enforce the right security controls to strengthen protection.
Risk-Driven Context for Immediate Action
Gain rich context through AI-driven classification for on-prem data. Understand sensitivity, compliance exposure, residency, security posture, and business context to prioritize what matters and reduce risk faster.
On-Prem Data Still Powers the Business.
It Shouldn’t Be a Blind Spot.
39% of businesses still store the majority of their data on-prem, but it remains vulnerable. Cyera provides deep visibility into your on-prem data with AI-powered classification, context, and risk identification to help you maintain even greater control.
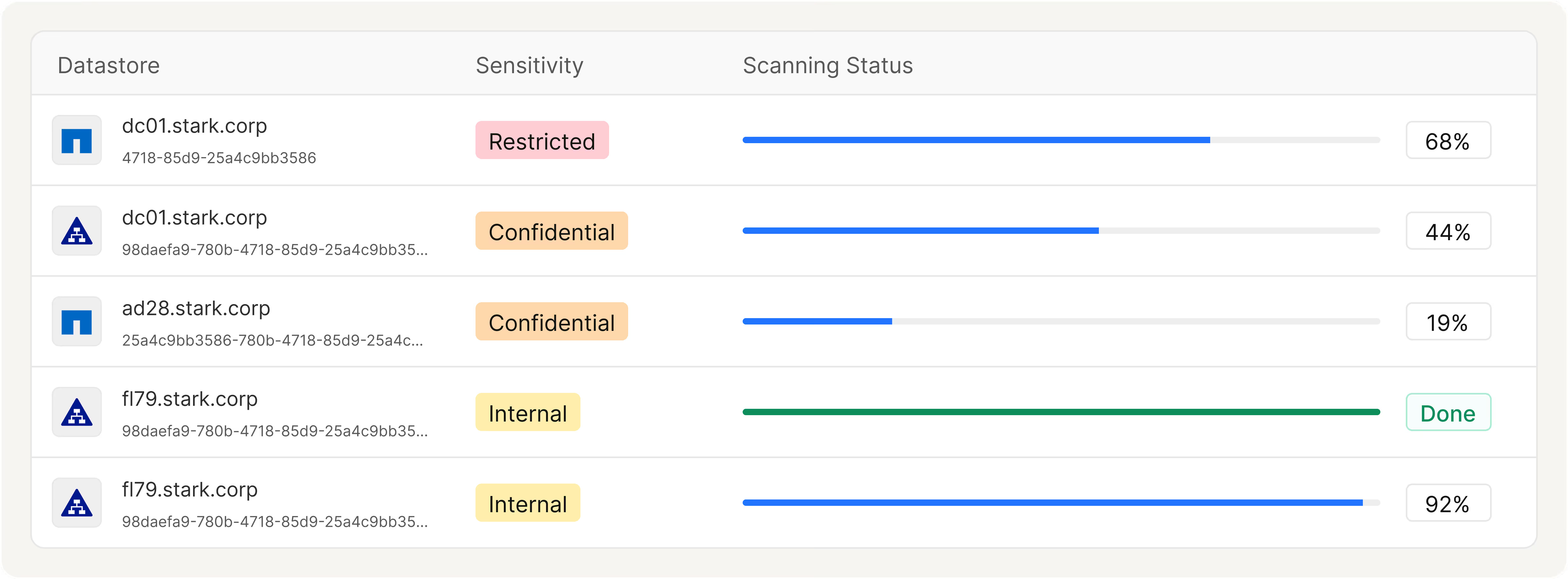
Rapidly Deploy DSPM On-Prem Without Operational Overhead
Get up and running fast with a lightweight deployment designed for on-prem environments. Cyera eliminates legacy agents and complex setups, so you see value immediately.
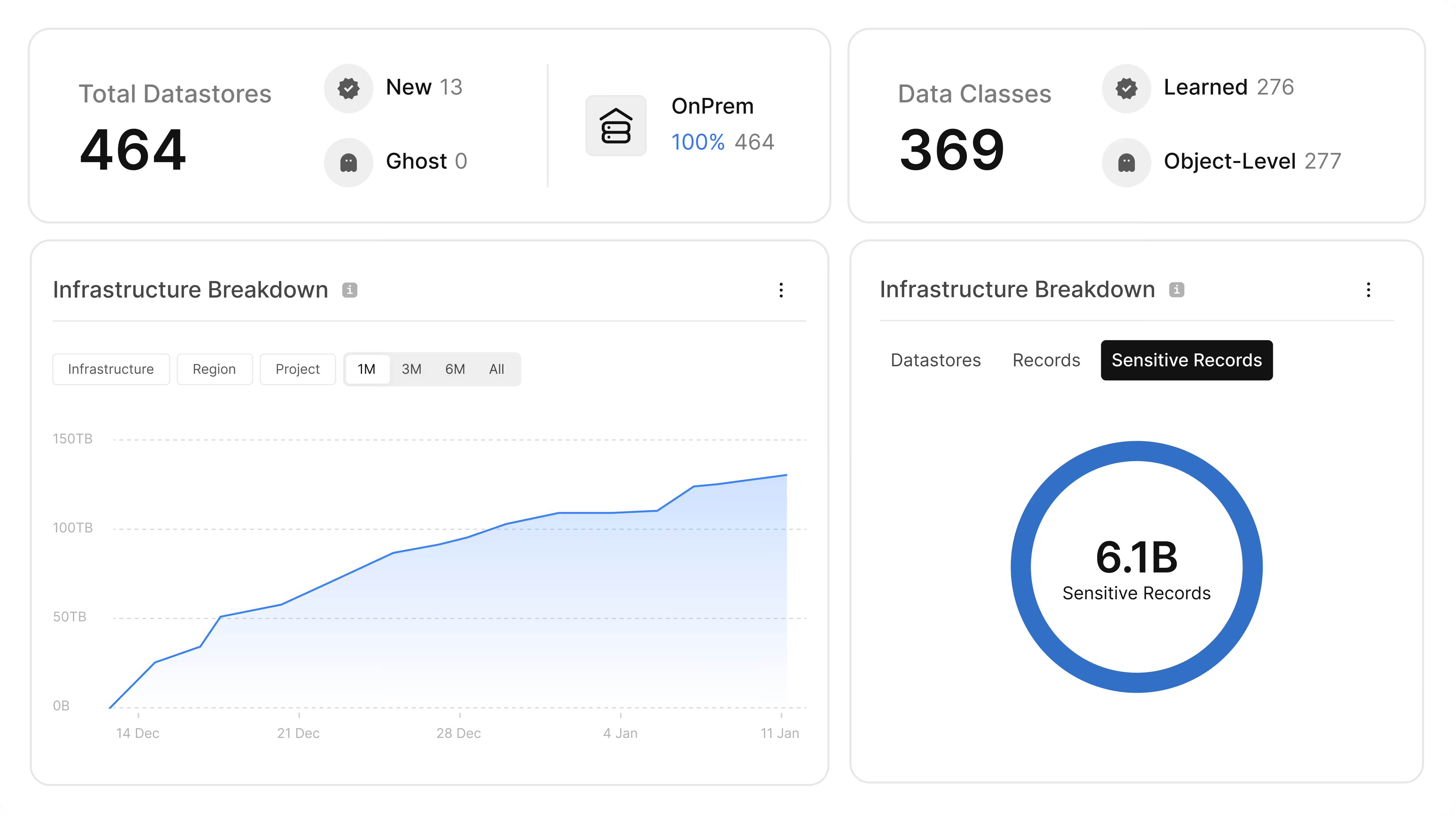
Rapidly Deploy DSPM On-Prem Without Operational Overhead
Get up and running fast with a lightweight deployment designed for on-prem environments. Cyera eliminates legacy agents and complex setups, so you see value immediately.
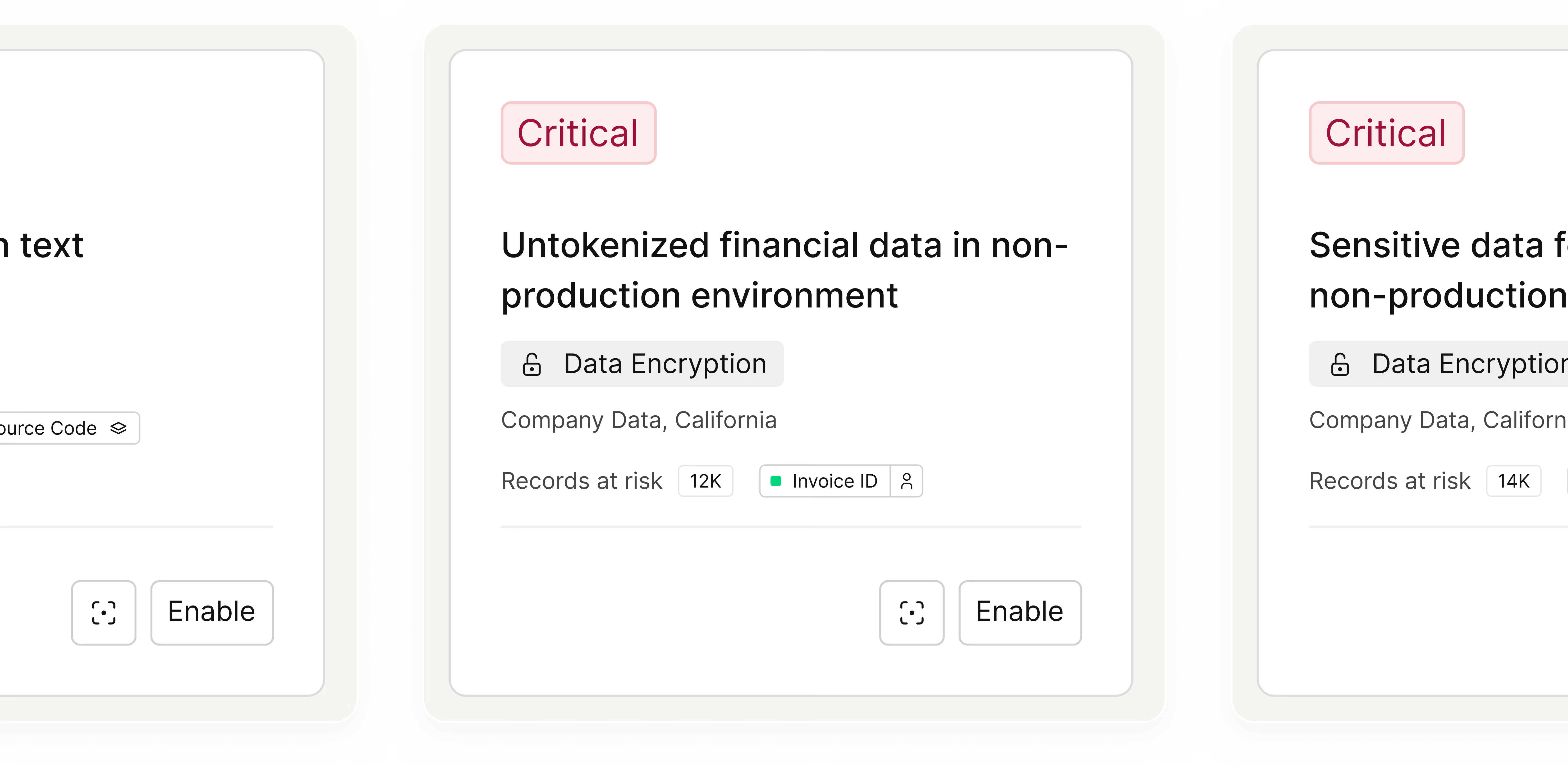
Uncover On-Prem Data Risks
Leverage AI-powered insights to uncover security gaps, enforce protections, and ensure compliance for your on-premises data.
FAQs
Cyera uses agentless discovery and AI-powered classification to scan on-premises databases, file shares, and application data. It identifies sensitive data types, relationships, and risk indicators without relying on heavy agents or manual rules.
Cyera supports both connector-based and connector-less deployment in SaaS or Outpost environments, giving you flexibility to meet your security and operational requirements. Our lightweight connector is easy to deploy and delivers significantly lower total cost of ownership than legacy connector- or agent-based solutions.
Yes. With Cyera’s Outpost deployment model, customers can keep data fully within their network and maintain complete control while still benefiting from Cyera’s AI-powered classification and context.
Cyera integrates seamlessly with SIEM, IAM, DLP, ticketing, and workflow systems to streamline detection, alerting, and remediation. On-prem findings can be operationalized across your established security stack.





.avif)

.svg)