Data Access Control
Enforce least privilege access at the data level.
























































































Identity Risk, Mapped Directly to Data
Permissions alone don’t complete the access risk equation. You need to understand the data itself. Cyera Data Access Control connects identities (human and non-human), roles, and permissions directly to the data they can access, revealing a new dimension of exposure risk and enabling precise least-privilege enforcement.
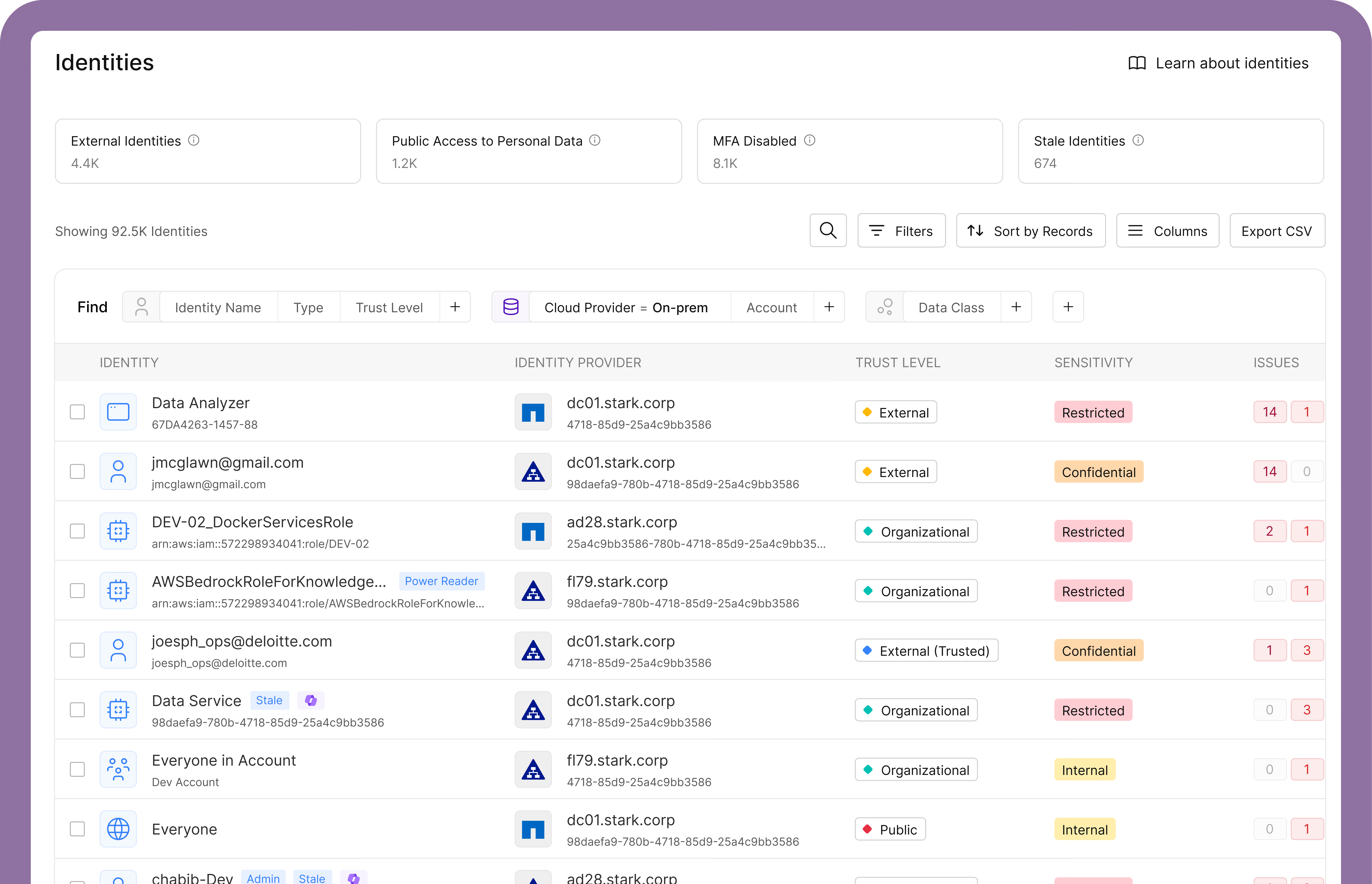
Reveal Access Exposure Through a Data-Driven Lens
Access understanding with data context leaves identity risk in the shadows. With Data Access Control, Cyera ties every human and non-human identity to the data it can reach across cloud, SaaS, and on-prem environments.
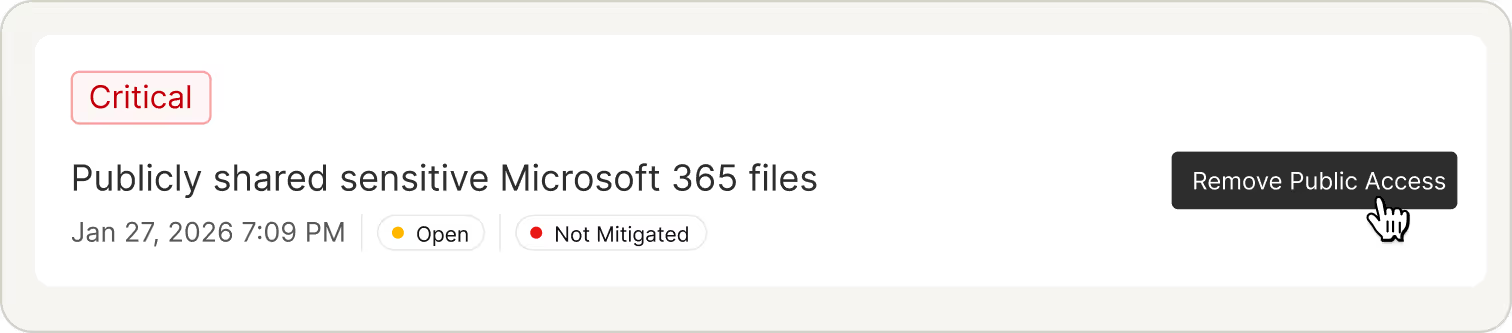
Eliminate Excessive Data Access
Over-permissioning creates silent exposure. Data Access Control identifies unused, excessive, and high-risk entitlements based on actual data sensitivity, helping teams remove access that should never have existed in the first place.
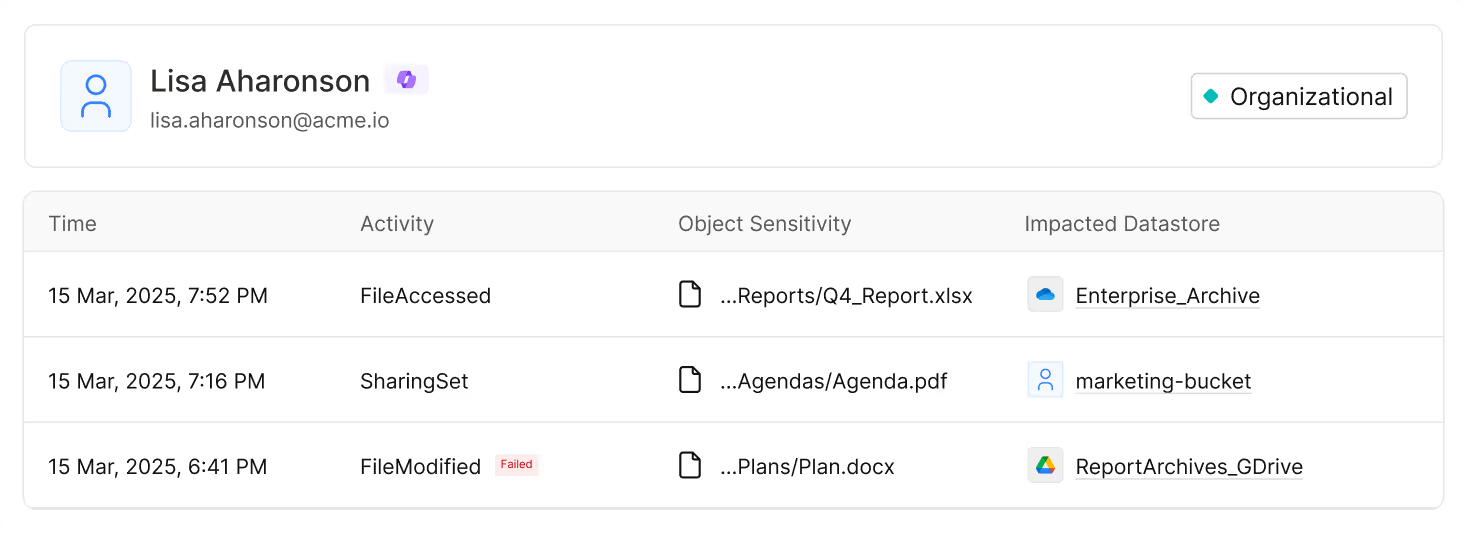
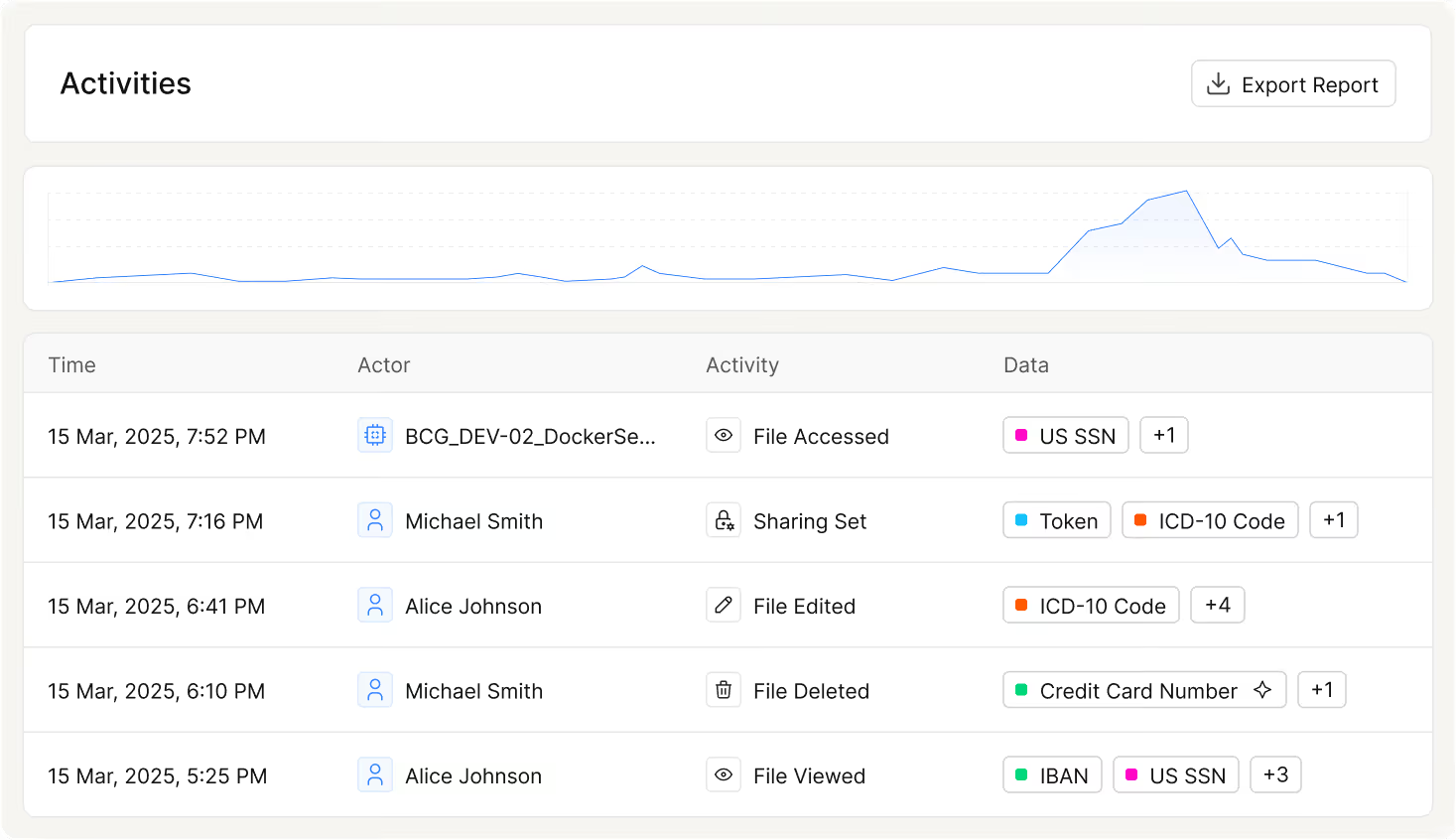
Where Data, Access, and Activity Converge
What could be accessed is a different question than what actually was. Data Access Control combined with activity tracking through our Access Trail capabilities provides a comprehensive view. Now, you can correlate activities with identities and data classifications, giving you the context to investigate and remediate insider risks fast.
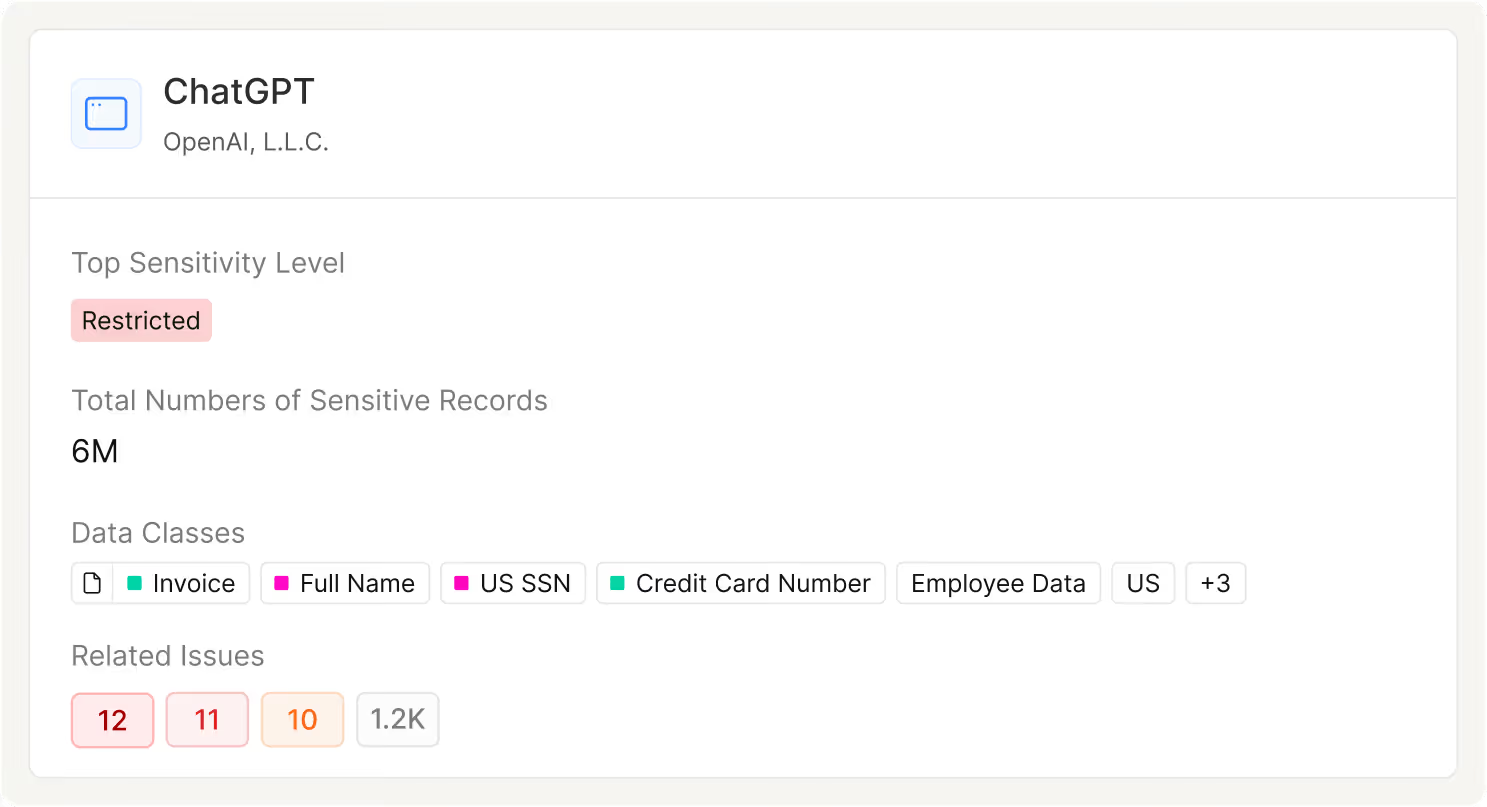
Control AI Data Access with Confidence
The fuel for AI is data, but it needs access to tap into it. This is breaking traditional access protections. Data Access Control brings AI users, tools, and agents into the same data-centric governance model, so innovation does not come at the cost of data exposure.

One Platform.
Explore More Cyera Products.
Identify and label data in discovered datastores with relevant data classes, and use context to determine the criticality of.

.svg)