Know Your Data, Control Your Access: How Cyera and AWS IAM Access Analyzer Deliver Data-Aware Governance for Sensitive Data in AWS

Unmasking Access: Why Data Security Starts with Identity Awareness
In today’s digital-first world, data is an organization’s most critical asset and its most targeted one. From customer information and intellectual property to operational insights and financial records, data powers business innovation and decision-making. As such, securing sensitive data is no longer a compliance checkbox, it’s a foundational pillar of trust, resilience, and long-term success.
Yet, as organizations move faster and embrace the scale of cloud infrastructure, the challenge of securing data has evolved. It’s not just about encrypting files or setting firewalls. It’s about understanding who has access to what and why.

The Identity-Data Visibility Gap
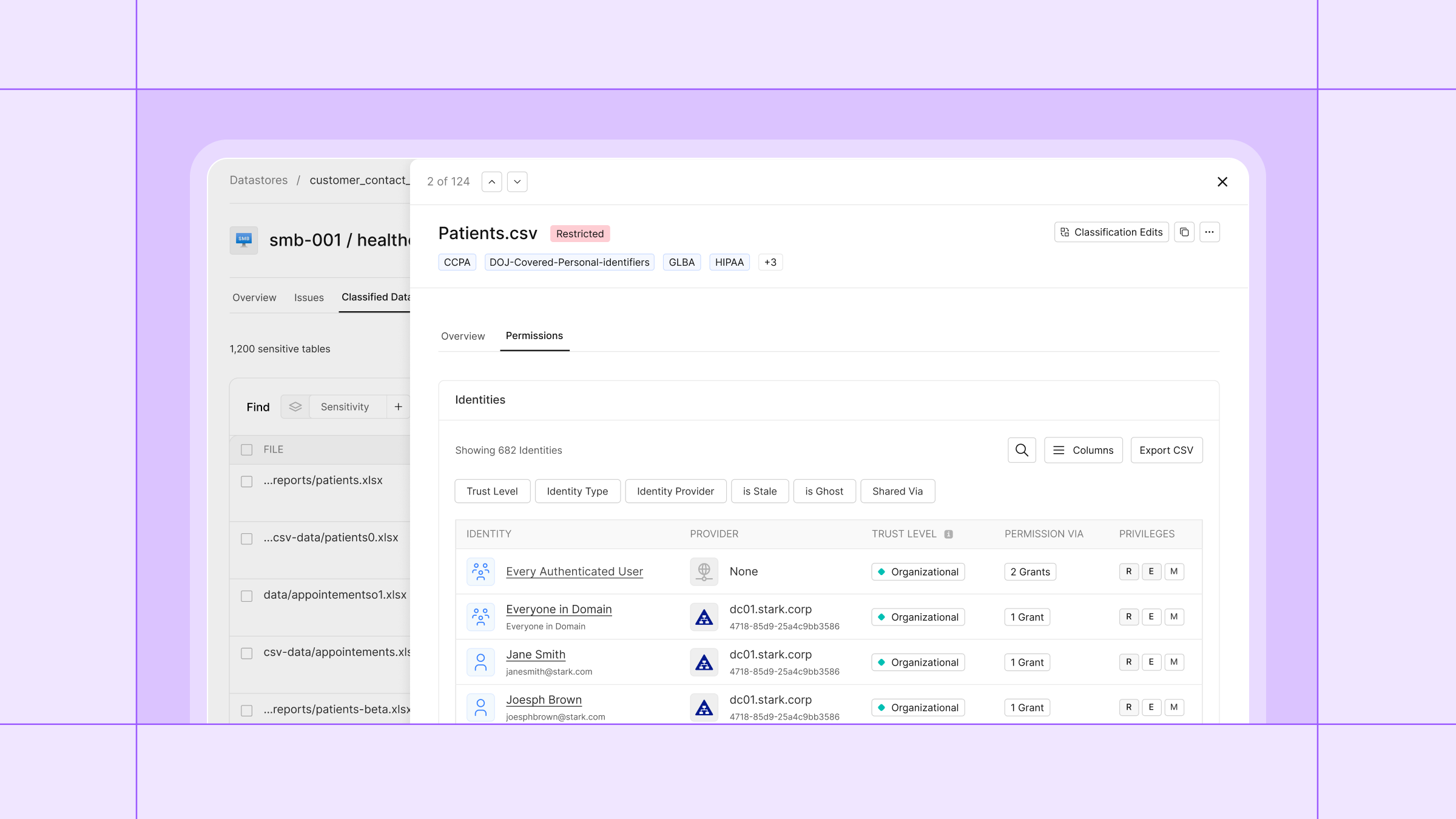
One of the most important challenges in cloud security today is the need for visibility into IAM (Identity and Access Management) configurations across sprawling, multi-account environments. For instance, answering the question “who can access what type of data?” is critical. In AWS, multiple IAM identities—users, roles, and federated entities—can be granted access to sensitive data stores such as S3 buckets, RDS instances, and DynamoDB tables. Some of these permissions are intentional, defined by policy. Others may be inherited, misconfigured, or the result of overly permissive roles or trust relationships.
The problem? It’s incredibly difficult to get a complete and accurate picture of all the identities that have access to a given datastore, especially when that data is highly sensitive. Compounding this, it’s just as hard to determine what level of access each identity actually has, whether it’s read-only, write, delete, or administrative, and whether that access spans a single AWS account or crosses account boundaries in complex organizational structures.
Why This Matters Now
The consequence of this data visibility gap is stark: organizations are blind to potential overexposure of their most valuable data. This not only increases the risk of insider threats and external breaches but also makes compliance with frameworks like GDPR, HIPAA, and PCI-DSS far more challenging.
At Cyera, we believe data security must begin with clarity—knowing where your sensitive data lives and who can access it. In this blog, we’ll explore how modern data security strategies help organizations bridge this gap by correlating identity, access, and data sensitivity at scale, empowering security teams to take decisive, risk-informed actions.
Bridging Visibility and Control with AWS IAM Access Analyzer
Amazon has enhanced IAM Access Analyzer with capabilities to detect internal IAM identities accessing AWS resources such as S3, DynamoDB, and RDS snapshots. These enhancements allow security teams to identify who has access to critical infrastructure.
When integrated with Cyera’s DSPM platform, which classifies sensitive data at scale, these IAM insights create a powerful combination. Teams gain context on whether access is valid or misconfigured, improving security posture and enabling prompt remediation.
Identity-Driven Data Security: Preventing Disclosure Through Insight
By correlating identity access with data classification, security teams move from theory to actionable insights. They can pinpoint which users, roles, or services have access to sensitive data (e.g., PII, PHI, intellectual property) and proactively mitigate risks.
This alignment makes IAM controls measurable and auditable. Instead of managing IAM in a silo, organizations gain a real-time map of data access.
Cyera Identities: Elevating Contextual Access Intelligence
Cyera’s Identities module maps access to S3 buckets classified by Cyera’s DSPM engine, providing the what (sensitive data) and the who (IAM identities).
As data expands to structured formats in DynamoDB and RDS, extending this insight becomes essential. Supporting access mapping across multiple AWS resources enables scalable, organization-wide governance.
What This Blog Will Show You
We’ll show you how to use IAM Access Analyzer to detect access to Cyera datastores and correlate these insights with data sensitivity. This approach helps uncover excessive access, enforce least-privilege principles, and protect sensitive data—no matter where it resides.
High Level Implementation Steps
Step 1: Create an Internal IAM Access Analyzer
Deploy an IAM Access Analyzer scoped to the AWS Organization in the master account. This ensures centralized visibility into cross-account permissions.
Step 2: Retrieve Analyzer Findings
Use the `retrieve-findings.sh` script to collect access details across analyzers. The findings are saved into `finding-details.csv`.
Step 3: Correlate with Cyera Datastores
Match findings (e.g., RDS snapshots related) to corresponding Cyera-scanned resources to determine their sensitivity classification.
Step 4: Generate the Permissions Matrix
Execute `generate_permissions.py` to create a `permissions_matrix.csv` showing IAM access against sensitivity levels.
Step 5: Analyze and Visualize
Import the matrix into tools like Amazon QuickSight or Excel to filter and visualize which IAM entities have access to sensitive datastores.

Sample scripts can be found here: cyeragit/AWS-IAM-Access-Analyzer-samples: Public repository to demonstrate the use of AWS IAM Access Analyzer CLI with Cyera DSPM platform
Conclusion
Organizations using Cyera’s DSPM platform can now bolster data governance by integrating AWS IAM Access Analyzer. This is particularly relevant for mitigating risks in environments where sensitive data is inadvertently exposed or leveraged for AI training.
By correlating identity and sensitivity, teams can confidently:
- Detect excessive or misconfigured access
- Enforce least-privilege access
- Maintain compliance
Whether you're a cloud security engineer, data governance lead, or compliance officer, this integration empowers you to answer a critical question:
Who has access to my sensitive data, and what level of access do they have?
Gain full visibility
with our Data Risk Assessment.