Spot and Prevent Insider Threats
Connect sensitive data to users and behavior to surface insider risk and trace unauthorized data movement across cloud, SaaS, and on-prem environments.
.svg)























































































See the Insider.
Stop the Risk.
Most insider threats happen when legitimate access is misused. Traditional tools flood teams with alerts but cannot show when sensitive data is actually at risk. Cyera connects data sensitivity, user permissions, access behavior, and data movement to pinpoint real insider threats and guide confident response.
Limit Access to What Matters
Too much access creates silent risk. Identify users, roles, and applications with access to sensitive data to expose excessive, inherited, or unused permissions so you can remove risk before it is abused.
Monitor How Sensitive Data Is Used
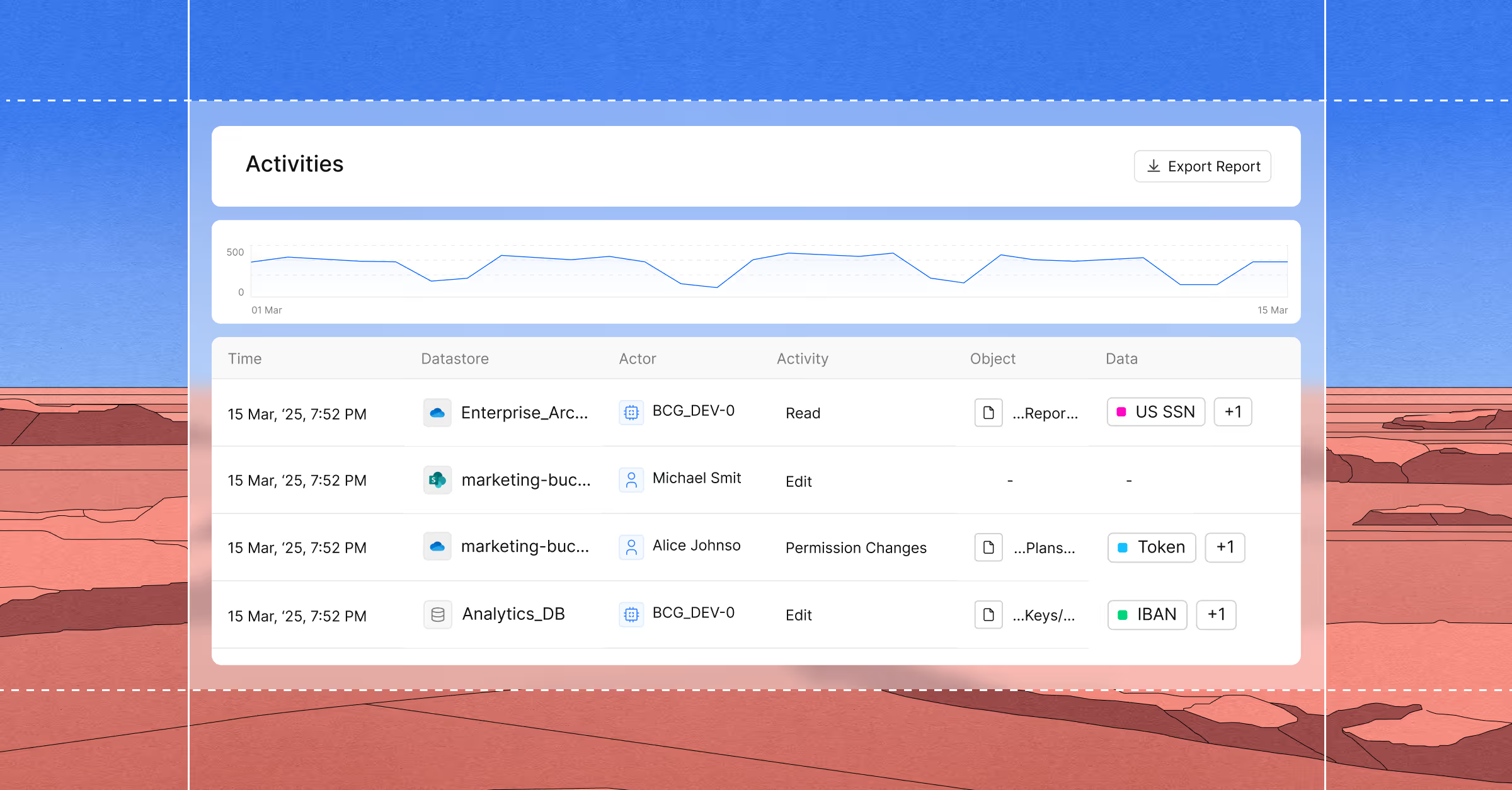
Track how users interact with sensitive data, including access volume, frequency, paths, and actions. Surface unusual or high-risk behavior that signals potential insider misuse.
Stop Unauthorized Data Movement
Detect and block risky downloads, sharing, and transfers of sensitive data using data-aware DLP controls before sensitive data leaves your environment.
Insider Threats Hide in a Flood of Alerts
Without identity, activity, and data context, most tools generate noise instead of answers. Cyera shows who accessed sensitive data, how they gained access, and what they did with it so teams can act with confidence.
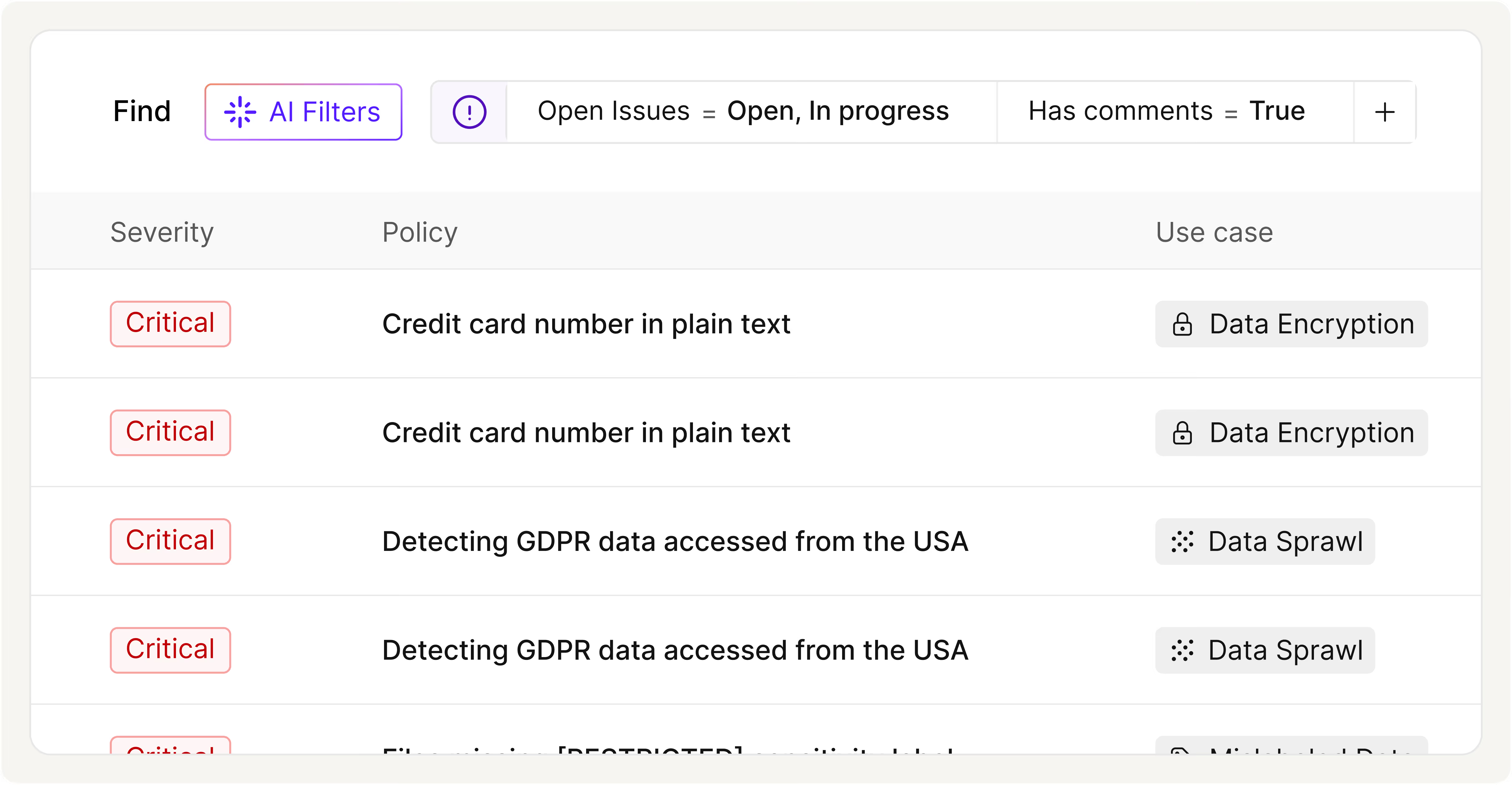
Understand Risk From Every Dimension
Insider threat investigations start with context. Cyera links activity to business context to reveal who accessed sensitive data, how they did it, and what impact that access has, giving teams a complete picture fast.
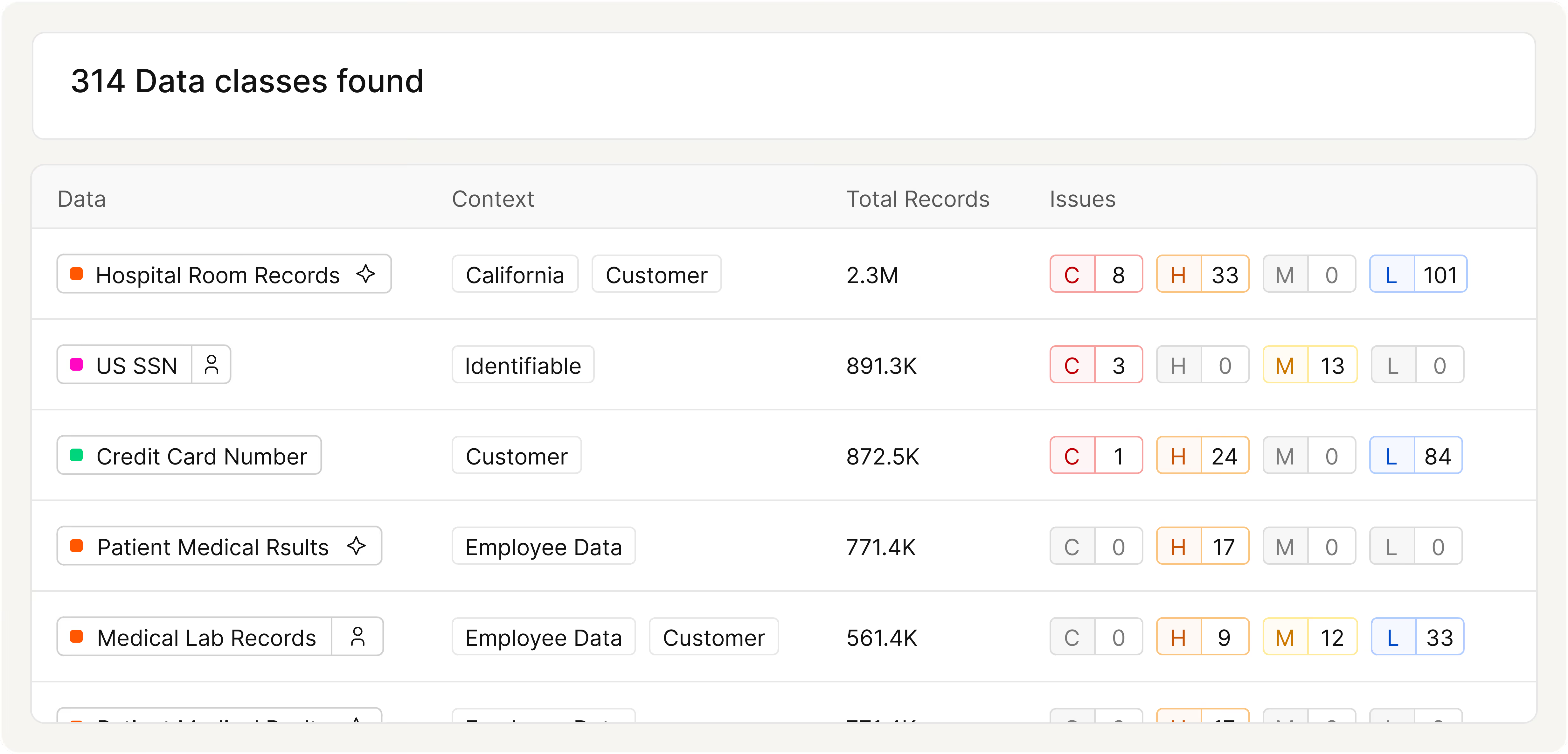
Investigate Insider Activity Instantly
Slow investigations leave risk unresolved. Cyera tracks access events with classification and identity context to uncover intent and behavior quickly, helping teams investigate insider misuse with speed and confidence.
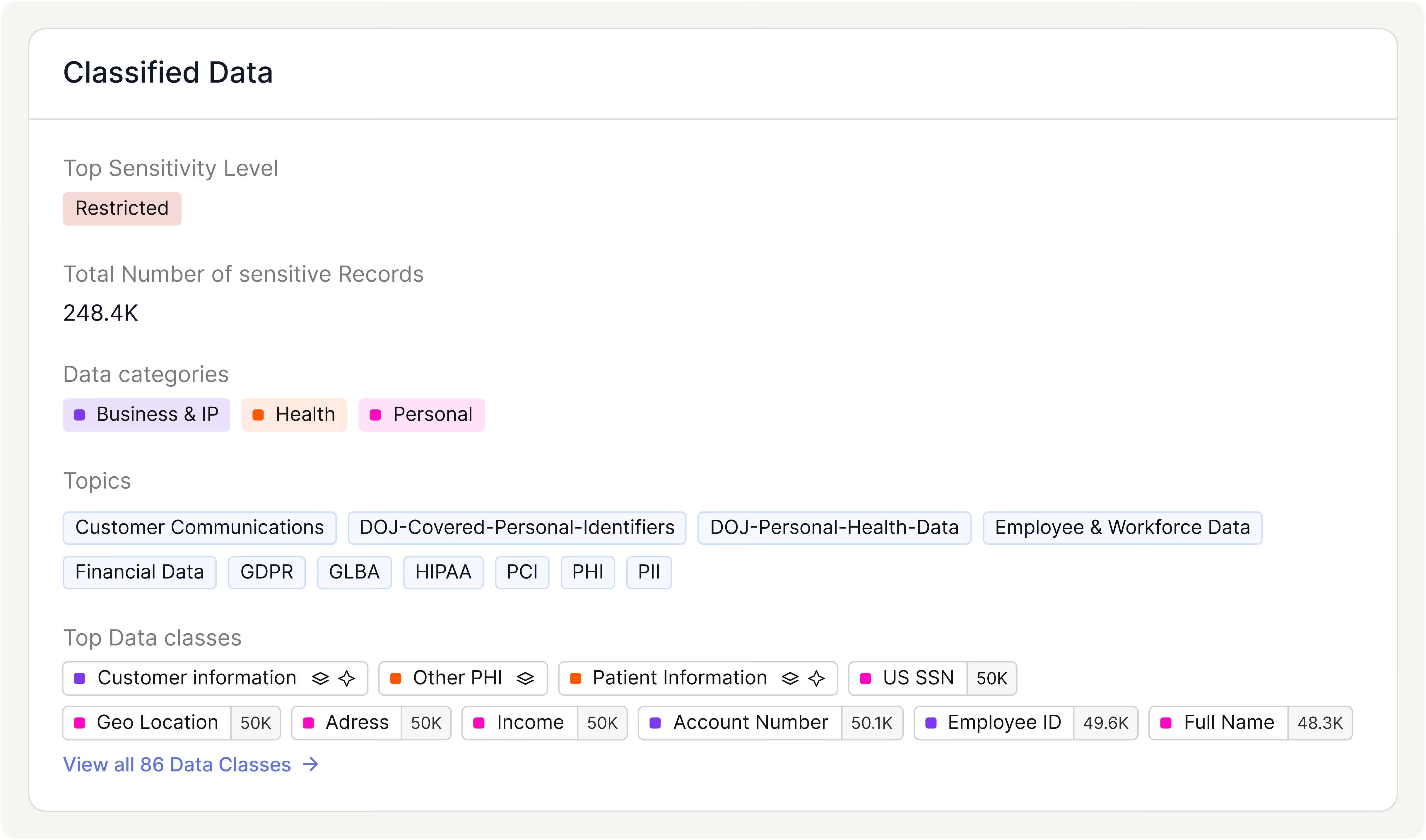
Gain Confidence Through Precise Classification
Access logs mapped to poor classifications consumes time and leaves insider threats unchecked. With Cyera, prioritize only what matters most with the confidence needed to act.
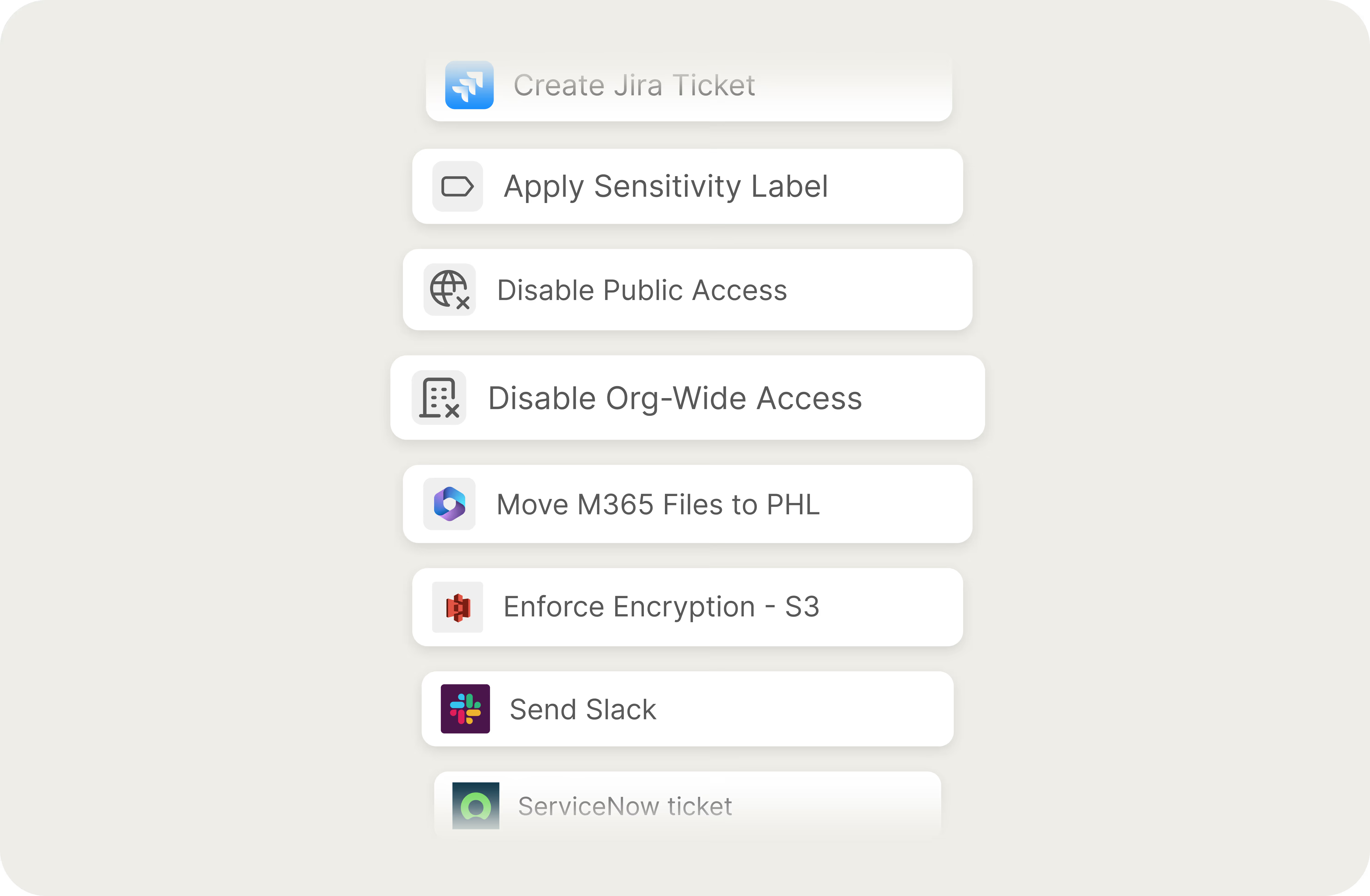
Reduce Insider Risk with Native Remediation Actions
Seeing is not enough. Cyera offers native remediation to remove unnecessary access, block risky data movement, and enforce least privilege without disrupting the business.
FAQs
Cyera detects insider threats by connecting sensitive data to identities, permissions, and usage behavior. Instead of relying on alerts alone, Cyera shows when legitimate access creates real data risk.
Traditional UEBA and SIEM tools focus on events and alerts. Cyera focuses on data. By tying user behavior directly to sensitive data, Cyera reduces noise and highlights insider activity that actually matters.
Access Trail provides a complete record of who accessed sensitive data, how they gained access, what actions they took, and when. This gives teams clear timelines and defensible evidence for fast, confident investigations.
Yes. Cyera traces sensitive data access, downloads, sharing, and transfers across cloud, SaaS, and on-prem environments so teams can understand scope and impact immediately.
Cyera provides clear identity and data context so teams can take targeted actions. This includes removing unnecessary access, enforcing DLP policies, and documenting evidence for audit or HR review.
Yes. Cyera provides defensible evidence linking identities, access, and data activity, helping teams support compliance, audits, and internal investigations with confidence.


.svg)