Cyera Access Trail
Know who accessed data.
Stop who shouldn’t.
Track every touchpoint with your sensitive data. Every identity, every activity, humans and AI.
Get a demoThe Data and Access Disconnect
Visibility Gaps Persist
Organizations may be able to answer who can access data, but don’t know who actually did. And when access activity relies on poor data classification, false positives consume time.
Event Volume Overload
With massive access events happening every day, most tools can’t identify which activities actually present business risk due to endless logs without business context and precise classification.
Slow Audits and Investigations
Teams spend weeks collecting and reconciling access evidence for audits and investigations, often producing incomplete or inconsistent results.
Your Smart Data Access Detective
By unifying data, identity, and access activity in one view, Access Trail correlates every access event with data sensitivity and ownership, enabling faster response, stronger governance, and continuous compliance.
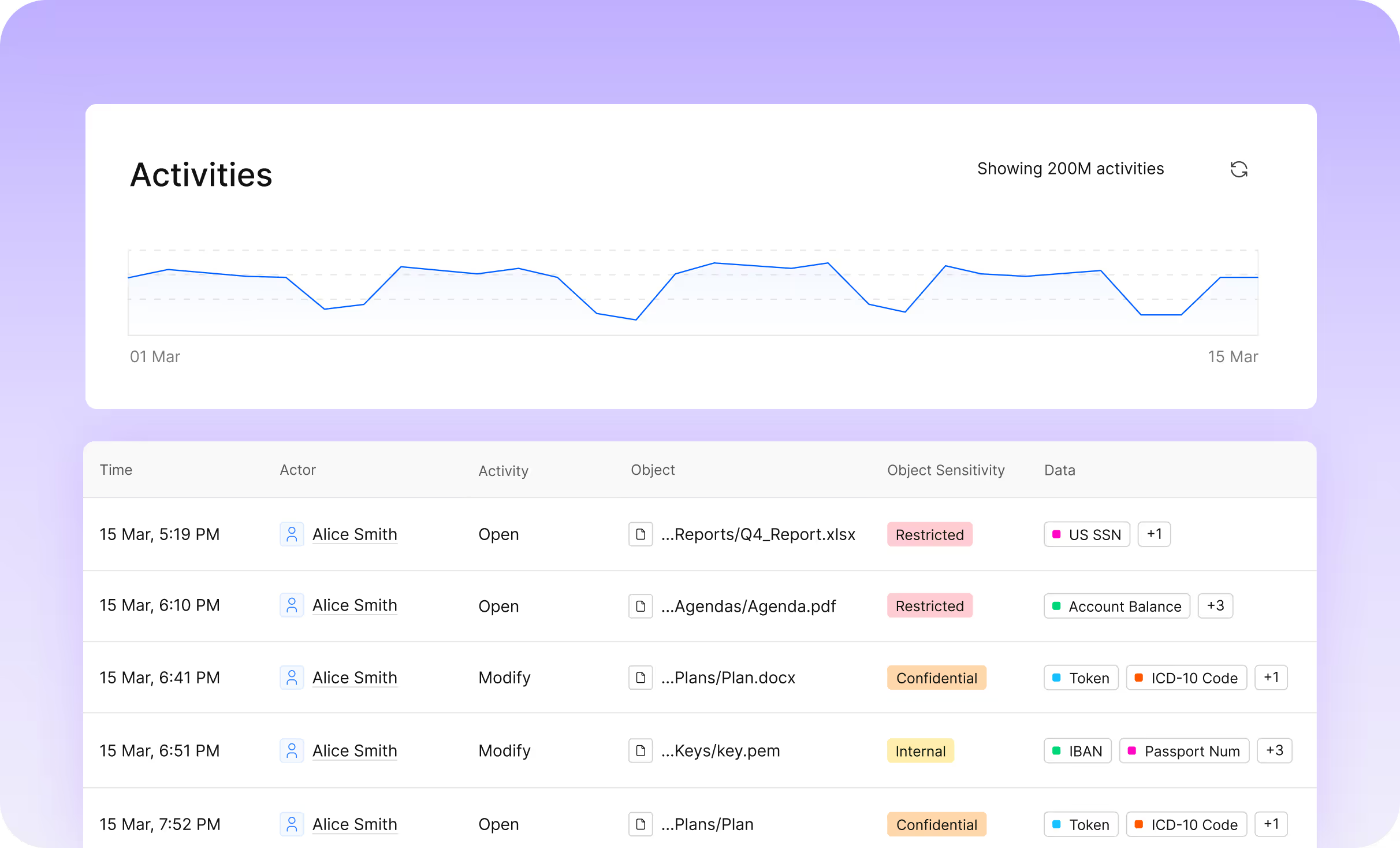
Capture Every Access Event, Human and AI
- Track every user, system, and AI interaction with your data.
- Monitor who accessed what, when, and how with precise data classification.
- Rewind any access activity to accelerate investigations and audits.
Prove Compliance with Evidence
- Generate verifiable records of every activity automatically, retained for a year.
- Replace manual audits with continuous, trustworthy reporting.
- Demonstrate that controls work and policies hold under pressure.
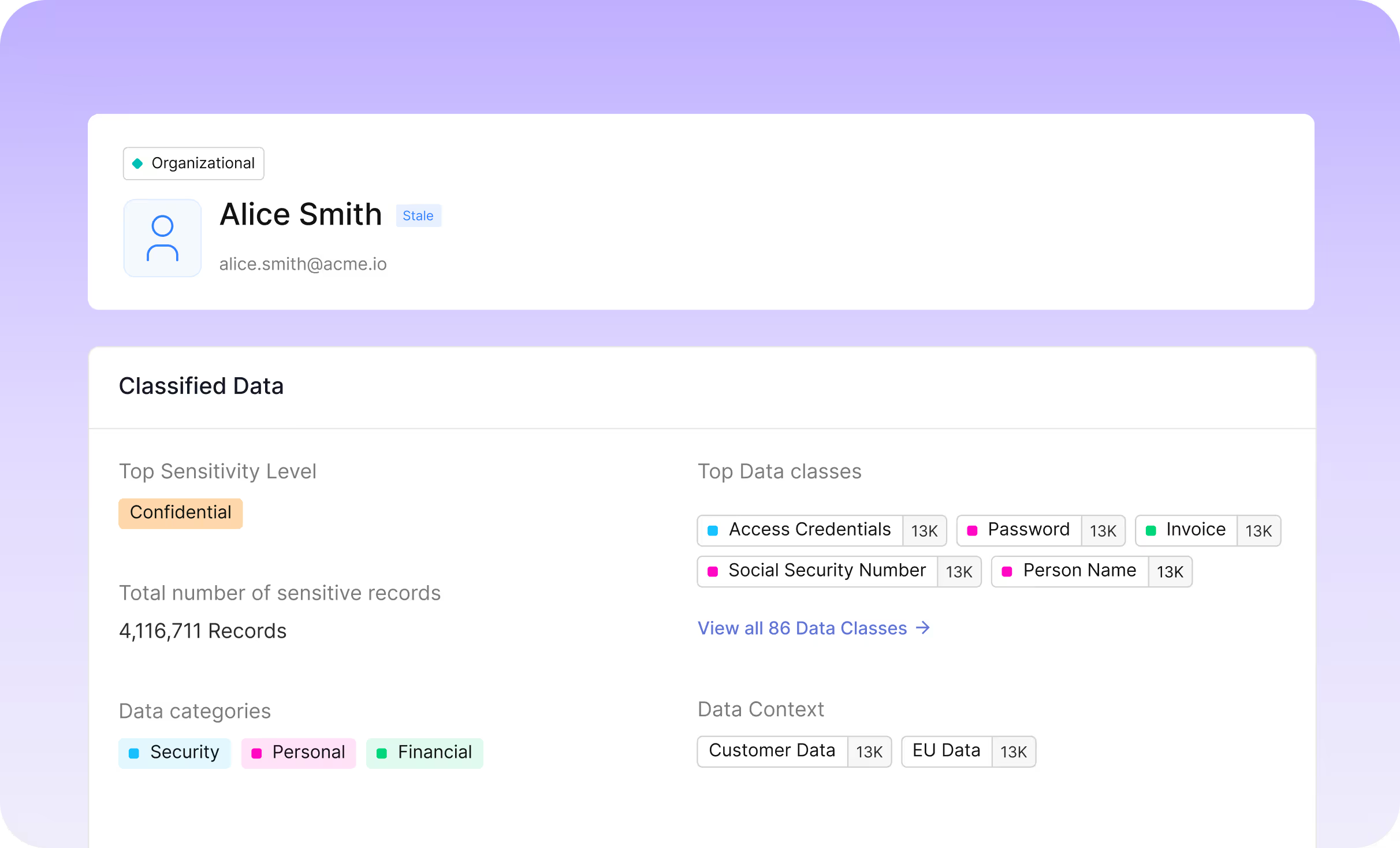
Investigate Insider Threats Faster
- Audit privilege misuse, data movement, and data drift quickly.
- Uncover hidden risks by correlating access with data sensitivity.
- Remediate insider threats by automatically revoking access with the context needed to prevent data loss.
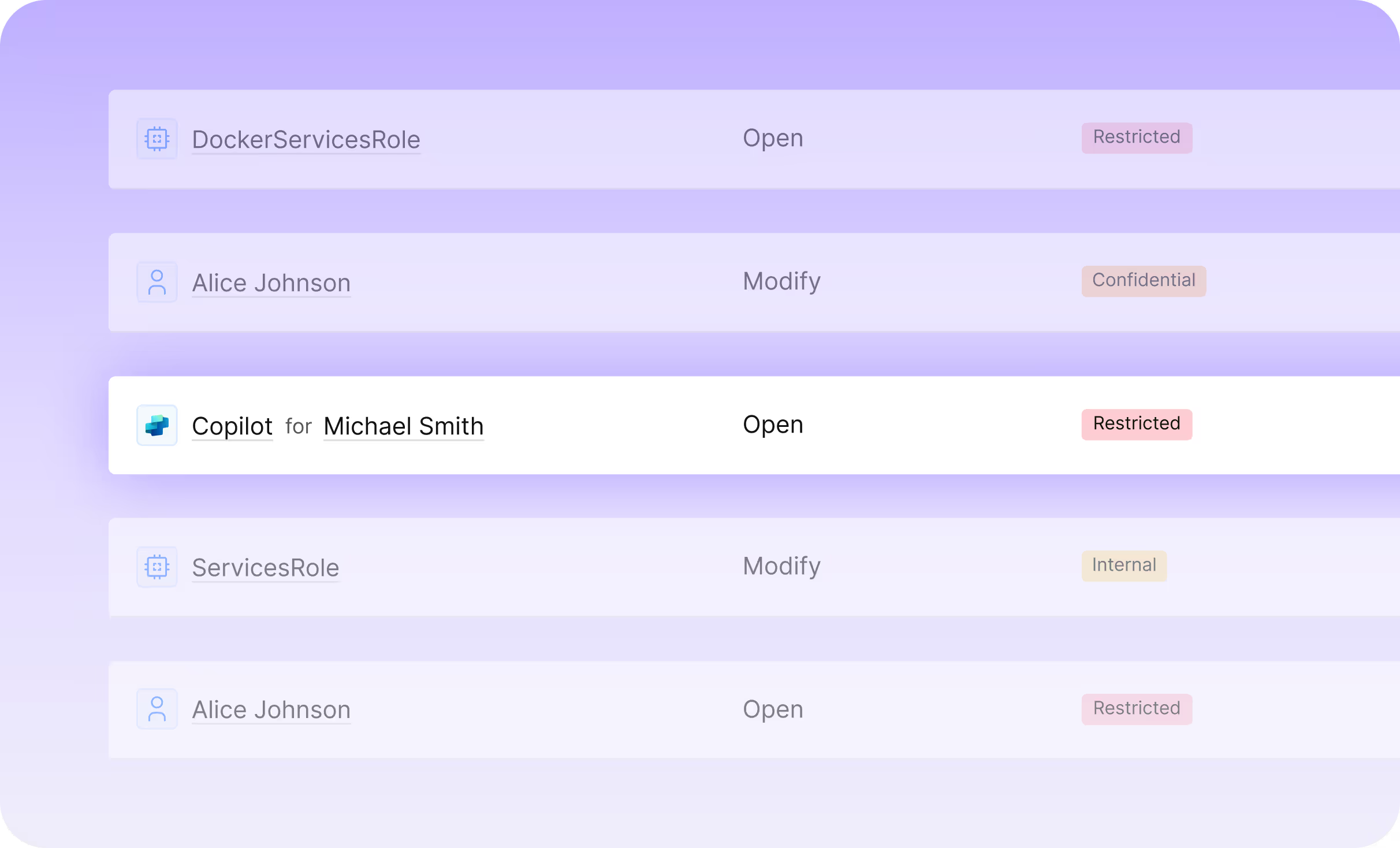
Uncover How AI Uses Data
- Understand how AI tools and agents use and transform information.
- Reveal intent, behavior, and potential misuse across AI-driven actions.
- Maintain access control and trust as AI becomes part of daily work.
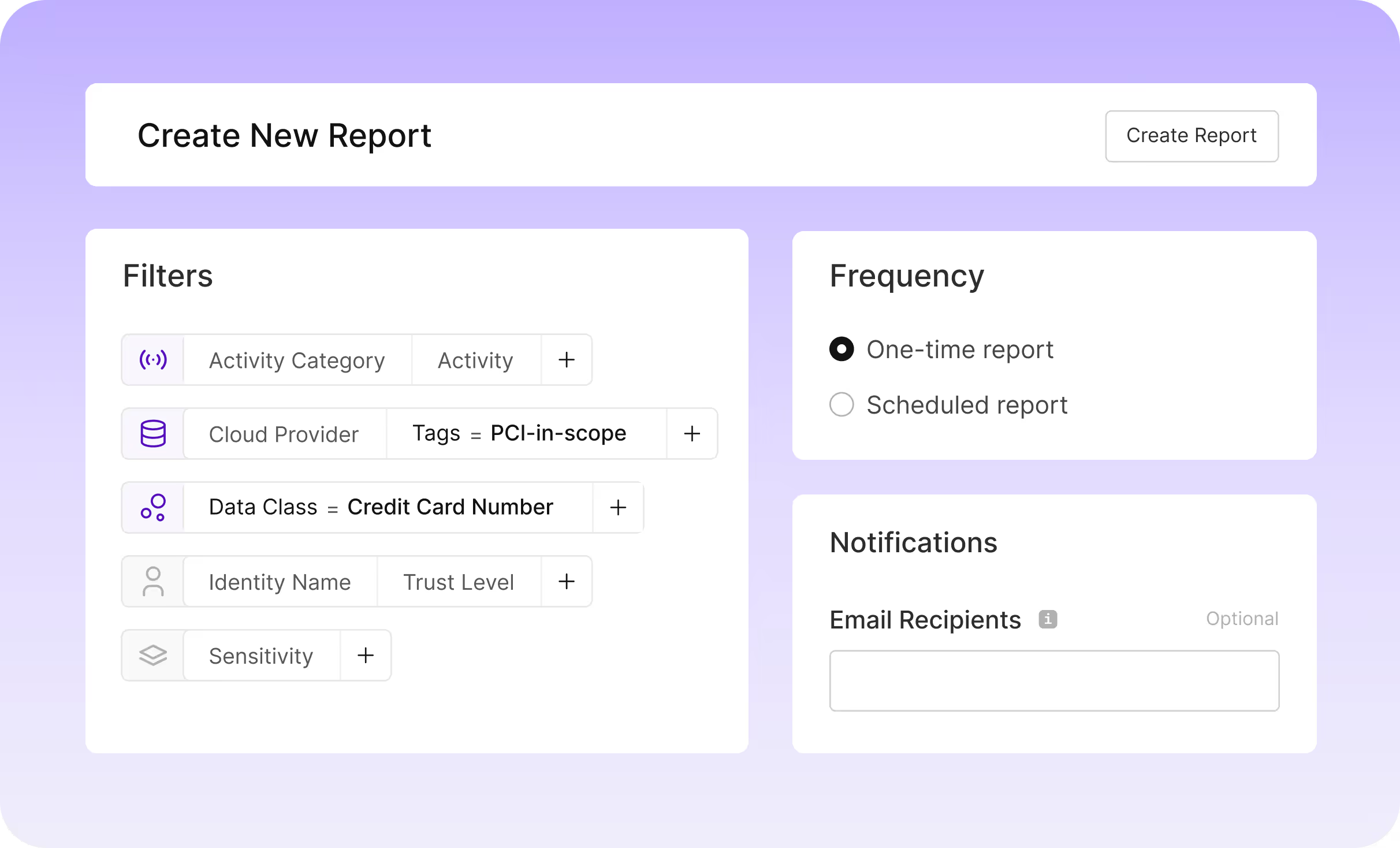
Reduce Risk Through Least Privilege
- Expose excessive rights by comparing entitlements with real usage.
- Find dormant or high-risk permissions across users and systems.
- Update access permissions with confidence to implement a zero trust approach.
A New Way to Understand Access
Audit Readiness
Provide audit-ready evidence quickly with confidence by automatically collecting and correlating access activity.
Insider Risk Investigation
Audit abnormal and improper access by insiders that present a risk to your business.
AI Activity Monitoring
Track how AI tools such as Microsoft Copilot interact with sensitive data to ensure compliant and secure use.
Access Rightsizing
Reduce exposure by uncovering and revoking unneeded entitlements.
Continuous Access Assurance
Maintain an always-on, auditable record of access to replace point-in-time audits.
Data Ownership Identification
Confirm accountable data owners to strengthen governance, improve data quality and security, and eliminate orphaned or unmanaged datasets.
Data Minimization
Find and remove untouched and unnecessary data to limit exposure, cut storage costs, and simplify governance.
A New Way to Understand Access
Audit Readiness
Provide audit-ready evidence quickly with confidence by automatically collecting and correlating access activity.
Insider Risk Detection
Detect abnormal or excessive access by users, admins, or AI agents before it becomes a security incident.
AI Activity Monitoring
Track how AI tools such as Microsoft Copilot interact with sensitive data to ensure compliant and secure use.
Access Rightsizing
Reduce exposure by uncovering and revoking unneeded entitlements.
Continuous Access Assurance
Maintain an always-on, auditable record of access to replace point-in-time audits.
Data Ownership Identification
Confirm accountable data owners to strengthen governance, improve data quality and security, and eliminate orphaned or unmanaged datasets.
Data Minimization
Find and remove untouched and unnecessary data to limit exposure, cut storage costs, and simplify governance.
Why Cyera?
AI-Native DSPM & Identity Foundation
Correlates every event with Cyera’s precise data classification and identity insights.
High-Performance Event Processing
Processes massive access activity streams in near real time with enterprise reliability.
Actionable Access Intelligence
Transforms raw access logs into actionable remediation scenarios.
Continuous, Not Static
Delivers ongoing visibility and historical context that adapt to business change.

.svg)

