Reign in Data Sprawl with Confidence
Sensitive data spreads; into SaaS, cloud misconfigs, and non-prod copies. Cyera continuously finds misplaced and non-compliant data so you can cut exposure and stay in control.
























































































Core Capabilities to Contain Data Sprawl
Data sprawl creates blind spots; whether its shadow stores, unmanaged SaaS, ghost backups, and non-prod copies. Cyera helps teams regain control and align protection to real risk.
Find Misplaced Sensitive Data Everywhere
Discover and classify sensitive data across cloud, SaaS, on-prem, and AI. Flag IP, PII, and PHI in unapproved locations before it’s exposed.
Prevent Risky Copies and Uncontrolled Data Movement
Locate hidden production data copied into dev/test/analytics. Enforce safer patterns (anonymized or synthetic data) and block spread to the wrong tools or regions.
Sustain Compliance and Governance at Scale
Map data to policy and regulation continuously. Spot non-compliant regions, unapproved systems, and over-retained data, and prove control.
Production Data Leaking into Non-Production Environments
Below are real-world scenarios we see every week. Each begins as a data sprawl problem, sensitive information silently drifting into the wrong places, and ends with Cyera providing the insight and controls needed to remediate risk and prevent it from returning.
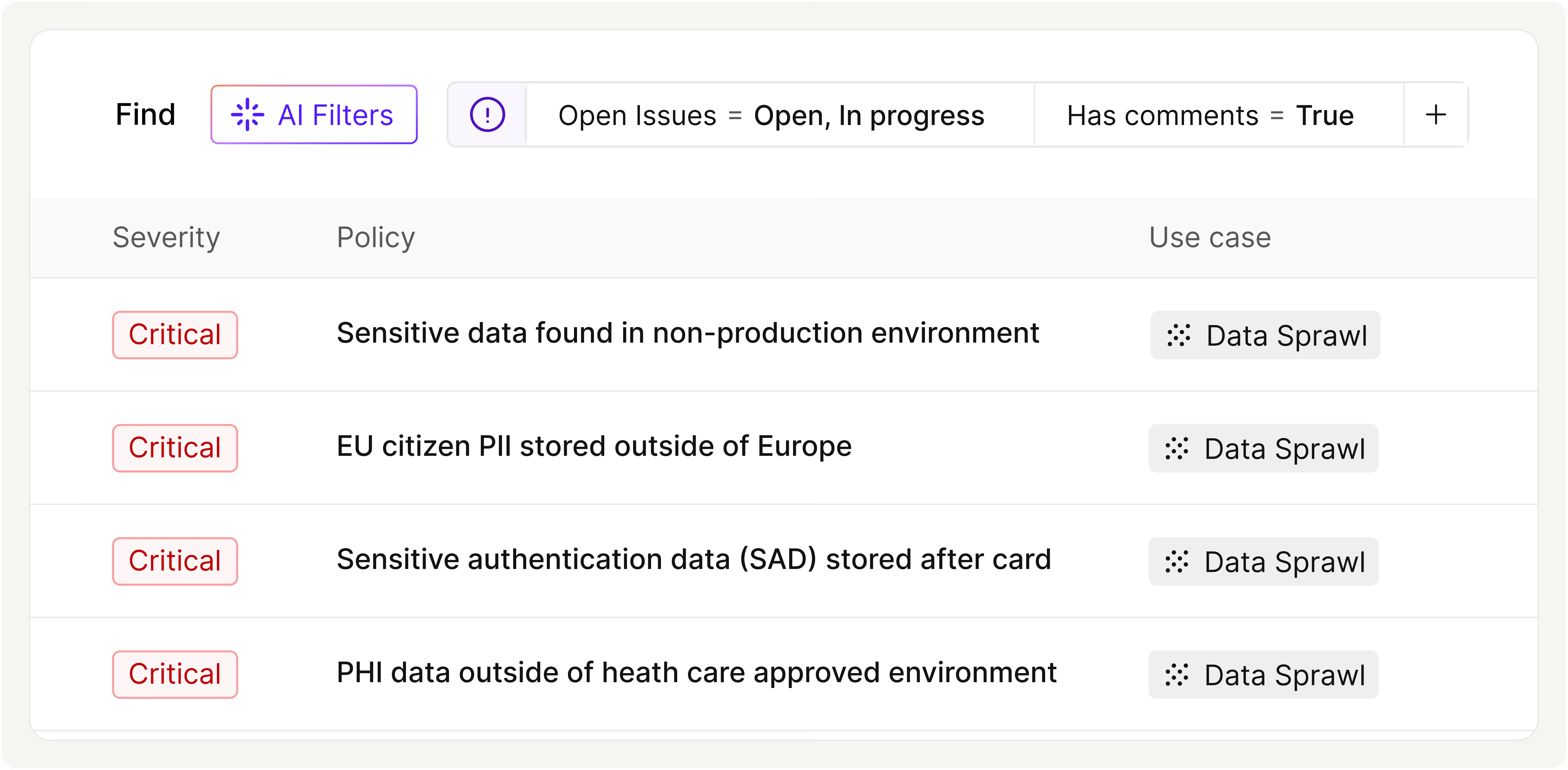
Detect and Stop Production Data Sprawl
- Automatically detect when production datasets are copied into dev, test, and sandbox environments.
- Identify real customer, patient, and employee records where only anonymized or synthetic data should exist.
- Enforce policies that prevent high-risk data types from being used in non-production systems and trigger remediation workflows when violations occur.
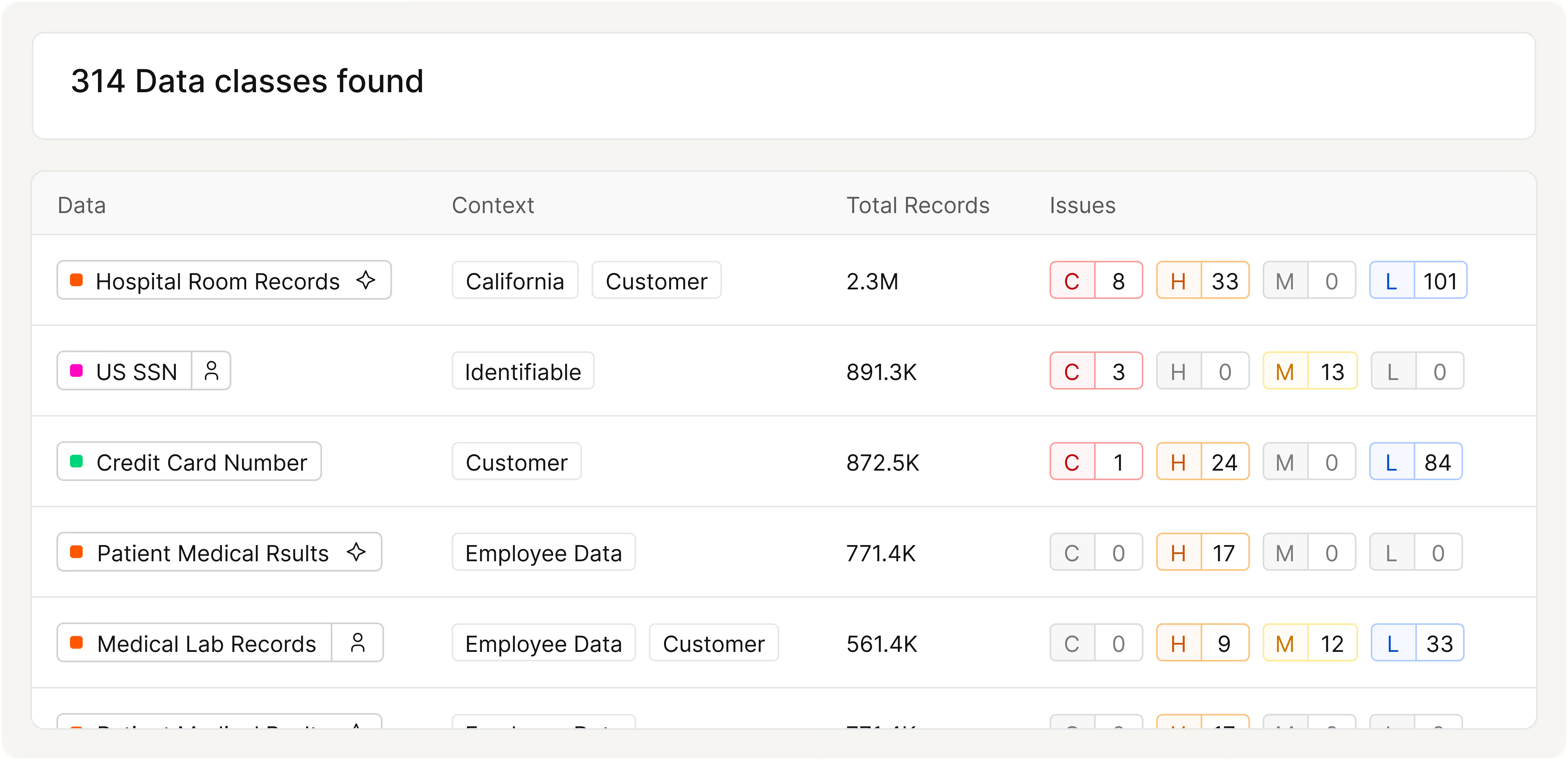
Expose Shadow Data and Ghost Copies Before Attackers Do
- Continuously scan for unmanaged data stores, snapshots, and exports that contain restricted data.
- Correlate each copy to its source system so you understand lineage, ownership, and purpose.
- Prioritize cleanup of ghost and redundant copies to reduce your attack surface and storage costs without disrupting the business.
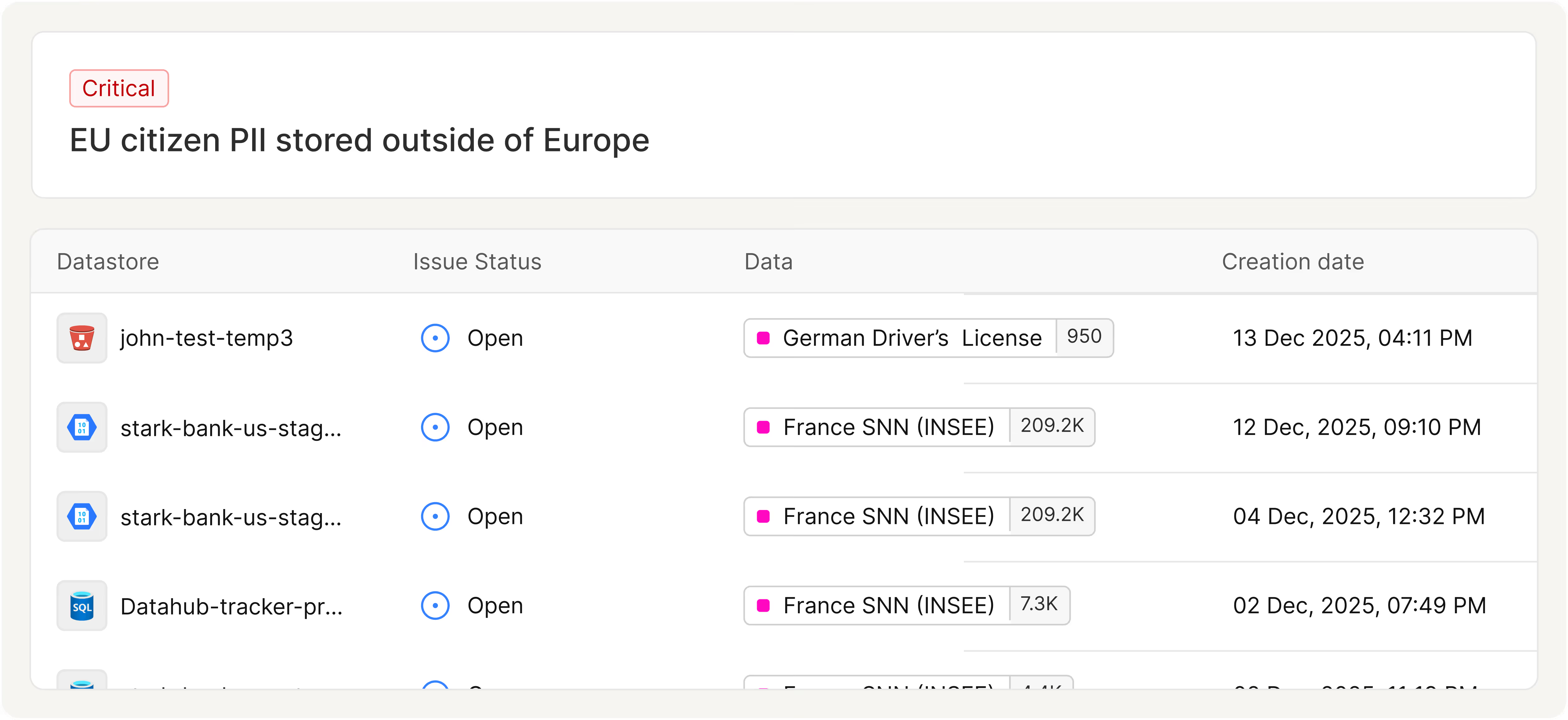
Keep Regulated Data Where It Belongs
- Continuously track where sensitive data is stored and processed across regions, providers, and services.
- Detect when data moves into non-compliant regions, unapproved SaaS applications, or risky third-party platforms.
- Provide auditors and regulators with clear evidence of localization controls, policy enforcement, and remediation.
FAQs
Data sprawl occurs when data is copied, shared, and stored across an ever-expanding set of systems, applications, and regions — often without centralized visibility or governance. As sensitive data spreads into unapproved locations, shadow systems, and unsecured environments, your attack surface grows dramatically. This increases the likelihood of data loss, insider misuse, or a breach, and makes it much harder to meet privacy and compliance obligations.
Cyera connects via APIs to your cloud providers, SaaS applications, data warehouses, and on‑premises systems to automatically discover and classify data wherever it resides. By understanding sensitivity, ownership, and business context, Cyera can flag when restricted data is stored in unapproved systems, non-production environments, or regions that violate policy. This continuous discovery gives security and privacy teams a unified view of legitimate datasets versus risky sprawl.
Not every copy of data is inherently bad. Cyera evaluates data locations against your security, privacy, and compliance policies, including approved systems of record, regions, and use cases. Copies that fall within those guardrails are treated as expected, while data in unapproved platforms, overly permissive repositories, or non-production environments is flagged as sprawl. This policy-based approach lets you focus on truly risky copies instead of every replica.
Cyera automatically recognizes non-production datastores and identifies when they contain sensitive production data such as customer, patient, or employee records. You can define policies that restrict which data types are allowed in these environments and trigger alerts, tickets, or automated remediation when violations are detected. This enables teams to maintain fast development cycles while ensuring that unsafe data never powers testing or experimentation.



.svg)