Cyera Named a Leading Platform in the Emergence of Agentic Data & AI Security

The security industry is at an inflection point. As artificial intelligence becomes woven into the fabric of enterprise operations, data has taken center stage in both opportunity and risk. Software Analyst Cyber Research (SACR) calls this the rise of Agentic Data Security—where data intelligence, identity context, and AI runtime control converge to form the foundation of the next generation of enterprise defense. The lines between data, identity, and application logic are dissolving, redefining how enterprises must design for trust in the AI era.
Recognizing this shift, SACR has named Cyera a leading platform in the rise of Agentic Data and AI Security, a new category that unites data visibility, protection, and AI governance under one control plane. Their latest research explores how the convergence of Data Security Posture Management (DSPM), Data Loss Prevention (DLP), and AI Security is reshaping enterprise security architectures. In this report, Cyera is highlighted for advancing that convergence through its unified approach to data intelligence and real-time enforcement, designed to secure how AI systems and agents use enterprise data.
Recognition from Software Analyst Cyber Research
Software Analyst Cyber Research positions Agentic AI Security as the next defining frontier in cybersecurity. Their team identifies Cyera, along with a select group of data and AI security leaders, as helping enterprises prepare for a new reality: one where autonomous and semi-autonomous AI agents continuously interact with business data.
The report highlights that while early data security tools like DSPM and DLP provided visibility and enforcement, the next wave must go further. As agents and copilots make decisions, generate outputs, and act on sensitive data, organizations need adaptive controls capable of governing these behaviors in real time.
Cyera is recognized for building toward that vision by unifying data classification, identity context, and runtime control to help enterprises safely embrace AI-driven operations.
A New Security Challenge: Understanding Agentic AI
Agentic AI represents a new phase of artificial intelligence. Unlike traditional models that simply respond to prompts, agentic systems can initiate actions, retrieve data, and make decisions across interconnected systems. They operate quickly and autonomously, often chaining tasks together or collaborating with other agents to complete goals.
This autonomy is powerful but also risky. Agentic AI expands the attack surface far beyond what traditional controls were designed to manage. The security challenge is no longer just preventing data exfiltration; it is understanding how AI agents use, share, and transform data across dynamic, multi-system environments.
This is where Agentic AI Security becomes essential. It focuses on visibility, governance, and control over autonomous AI activity.
Why Cyera Was Recognized
According to SACR, Cyera’s leadership stems from its ability to connect the dots between data, identity, and AI activity. The report highlights several differentiating strengths:
- Data Intelligence as a Foundation: Built on Cyera’s Data DNA engine, the platform provides deep context around data sensitivity, ownership, and exposure. This foundation enables high-precision visibility that informs AI controls.
- Unified Control Across Environments: By combining DSPM and DLP, Cyera delivers consistent policy enforcement whether data is stored, in motion, or being accessed by an AI system.
- Readiness for Agentic AI Security Risks: Cyera’s platform helps organizations discover and monitor how AI agents interact with sensitive data, enabling real-time insight into actions and exposure points.
- Operational Impact: Early enterprise deployments demonstrated reductions in alert noise, improved SOC response efficiency, and measurable visibility into AI and data access behavior.
The recognition reflects Cyera’s position at the center of a growing market consensus: securing AI starts with securing data.
“Single-point bets fail in the age of intelligent systems. Our research shows enterprises don’t succeed by choosing either identity, data, or AI security in isolation. The programs that work begin with truly knowing their data where it lives, what it is, and how it moves and then build upward. That foundation enables context-rich identity and access control, precise discovery and classification, lineage awareness, and runtime prevention capabilities that range from blocking and encryption to adaptive warnings. Without that depth of understanding, every other control layered on top loses effectiveness. Cyera’s approach reflects this reality, anchoring AI and identity security in deep data intelligence so organizations can evolve from static labels to adaptive, identity-aware, AI-ready security.”
— Aqsa Taylor, Chief Research Officer, Software Analyst Cyber Research
A Converging Future: Data, AI, and Identity
As the team at SACR notes, enterprises are entering a world where data, identity, and AI are inseparable. Sensitive information no longer simply lives in databases or travels through networks; it is now being interpreted and acted upon by autonomous systems.
This shift demands a unified approach to security, one that can understand not just where data resides, but how it is being used. Cyera’s work at this intersection positions it as a strategic enabler for enterprises seeking to operationalize Agentic AI Security with confidence and control.
From Convergence to Program Design: The Blueprint for an AI Security Program
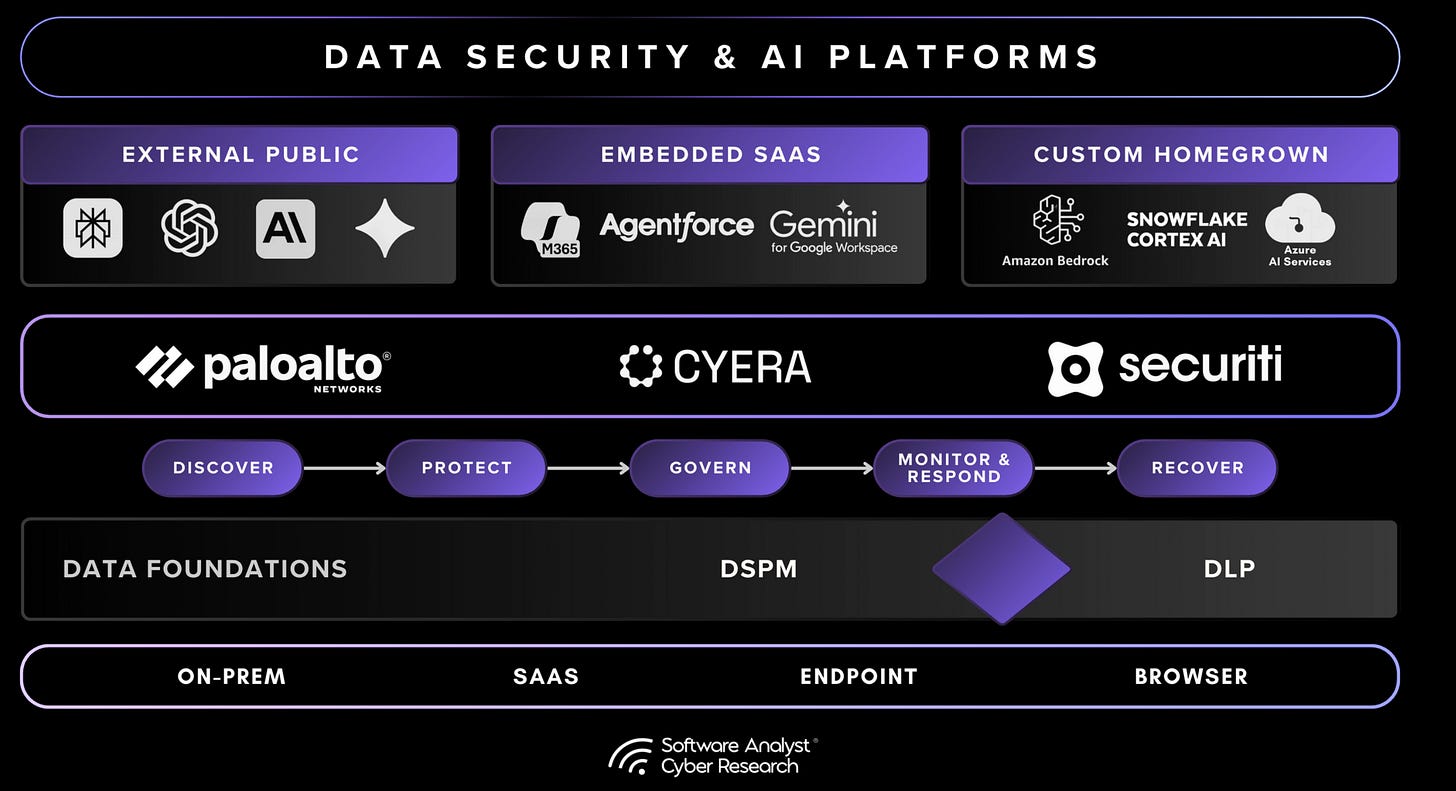
SACR’s research doesn’t just describe a market shift; it outlines the structure for an Agentic AI Security framework built for the agentic era. The same convergence of DSPM, DLP, and AI Security that analysts attribute to Cyera’s leadership also provides a practical roadmap for enterprise security teams.
Here’s how organizations can evolve from static data protection toward a living AI Security framework.
1. Establish the Foundation: DSPM + DLP
Every effective AI security strategy starts with data visibility and control. DSPM maps your sensitive data landscape, creating high-fidelity context around ownership, classification, and exposure. DLP enforces those rules as data moves, ensuring consistent protection across endpoints, SaaS, and networks.
Together, these create the data foundation for AI Security. SACR refers to this as the “intelligence layer,” a unified view of data sensitivity and behavior that prepares organizations for agentic control.
2. Discover and Govern AI Systems
Next, enterprises must extend visibility into the AI layer. This is where AI Security Posture Management (AI-SPM) comes in.
AI SPM continuously discovers AI systems such as copilots, embedded SaaS models, or custom internal agents, and classifies what data each can access. From here, the organization can begin governing agent behavior to:
- Detect and manage shadow AI
- Enforce least privilege for AI models
- Apply contextual policies to prompts and responses
Cyera’s AI Guardian, built on the Data DNA engine, operationalizes this by linking DSPM visibility with runtime policy awareness.
3. Monitor and Enforce at Runtime
Discovery alone isn’t enough. As AI systems act autonomously, runtime protection becomes critical. AI Runtime Protection (AIRP) extends the control plane into live environments.
It inspects prompts, responses, and data retrievals in real time.
It blocks unsafe actions or redacts sensitive data before exposure.
It enforces rules based on data type, user identity, and intent.
This is the active governance layer, the point where AI and data security truly converge. It ensures that every action an AI takes can be monitored, justified, or stopped.
4. Streamline Data Response and SOC Operations
Agentic AI Security doesn’t replace the SOC; it enriches it. By fusing DSPM intelligence with runtime telemetry, response teams gain context on who accessed what, how data was used, and whether an AI system was involved.
This enables:
- Faster triage and fewer false positives
- Automated enrichment of incident alerts
- Clear visibility into data lineage during investigations
As SACR noted in its analysis, early Cyera deployments reduced alert fatigue by over 70%, transforming SOC operations from reactive monitoring to proactive data defense.
5. Contain the AI Security Blast Radius
When incidents occur, the modern program must address AI’s unique blast radius, not just where data leaked, but how it was transformed or learned by models.
Recovery involves:
- Tracing lineage from original datasets to AI outputs
- Assessing what agents or copilots acted on that data
- Revalidating compliance and retraining where needed
By connecting data and identity context, the AI Security framework makes recovery measurable and auditable, restoring data trust and model integrity.
6. A Continuous, Adaptive Loop
Finally, an AI Security Program is never static. Each function - DSPM, DLP, AI SPM, AIRP, and response - feeds the next, forming a continuous control loop.
Discovery informs governance. Governance guides runtime control. Runtime insights refine response. Response improves discovery.
This adaptive cycle is what SACR Founder and CEO Francis Odum defines as agentic data security, a security architecture that reasons over both data states and data actions.
Looking Ahead
As enterprises integrate copilots and agentic systems into everyday workflows, security must evolve just as quickly. The convergence of data intelligence, identity governance, and AI runtime protection isn’t simply a technology trend; it’s the blueprint for trust in the AI age.
Cyera’s recognition by Software Analyst Cyber Research underscores both our momentum and the industry’s direction. As enterprises integrate AI copilots, autonomous systems, and task-driven agents into their operations, Agentic AI Security will define the next decade of cybersecurity strategy.
The organizations that succeed will be those that unify visibility, governance, and enforcement into a single adaptive layer that can move as quickly as AI itself. Cyera is honored to be recognized for leading that transformation and remains committed to helping enterprises adopt AI securely, responsibly, and at scale.




%25201200x628.avif)

.svg)