

Data Risk Assessment
Take the guesswork out of your corporate cybersecurity investments. Make informed decisions by identifying gaps in your data security posture, compliance, and overall security profile.
A comprehensive Data Risk Assessment by Cyera can provide you with the visibility needed to effectively mitigate potential risks and vulnerabilities.
.avif)
The Cyera Data Risk Assessment Service offers a turn key solution for evaluating your organization's data strategy and cybersecurity maturity. It provides a comprehensive, engaging, and practical approach to assessing your data management and security practices.
By leveraging over 30 critical controls, along with the powerful capabilities of Cyera's data security platform, OSINT, and Dark Web intelligence assets, we deliver actionable insights tailored to your specific operating environment. This process not only strengthens your data security strategy and cybersecurity posture but also aligns with your vision to effectively engage stakeholders and deliver value.
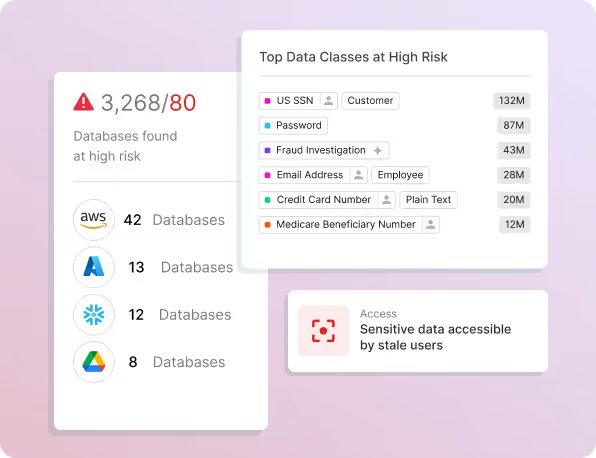
Assets Overview
Data stores, volume, growth, age.
Classification Overview
Sensitive data locations, data types, context types, file types.
Access Analysis
Top users with access, stale access, third-party access/sharing.
Data Risk Overview
Recommendations, peer comparisons based on industry/size/location.
1. Evaluation of Critical Controls
A virtual CISO-led evaluation of 30+ critical controls derived from established frameworks (COBIT 2019, DAMA-DMBOK, ISO/IEC 27001, NIST SP 800-53, NIST CSF) ensuring comprehensive coverage of data strategy and cybersecurity aspects relating to data.
2. Cyera Data Discovery & Classification Exercise
Leverage the power of Cyera's Data Security Platform to target a predefined number of Data Stores and/or volume of data for discovery and classification.
3. OSINT & Dark Web Discovery Exercise
Utilize OSINT and Dark Web intelligence resources to perform a discovery exercise on previous data breaches and leaks. Identify compromised credentials and other exposure details related to the in-scope organization.
4. External Attack Surface Discovery Exercise
Employ attack discovery and mapping resources to identify the public digital footprint of an organization. Highlight relevant cyber hygiene risks that could impact the data entrusted to the organization.
Product Features

95% classification accuracy
Provides identity data access insights
Supports any data across any environment
Auto-learning via proprietary AI-powered classification engine
Agentless deployment model

24/7/365 Monitoring and Validation
Alert triage & prioritization
Log & Network Analysis
Custom Reporting & Security Reviews
Vendor-agnostic Tooling



.svg)