Cyera Access Trail : suivez chaque interaction humaine et artificielle avec vos données
Tous les responsables de la sécurité connaissent l'exercice. Une enquête sur les risques internes commence ou un audit est lancé, mais les mêmes questions se posent toujours : qui a touché les données sensibles, qu'a-t-il fait, quand et surtout, en sommes-nous sûrs ? Les réponses devraient être simples, mais elles ne le sont jamais. La classification incorrecte et lente des données a laissé les équipes moins confiantes au lieu de les sécuriser. Et aujourd'hui, les outils et les agents d'IA ne font qu'ajouter au défi.
Sans une visibilité complète de l'activité d'accès et de la sensibilité des données sous-jacentes, les politiques de moindre privilège échouent, les menaces internes sont ignorées et les audits restent des marathons manuels.
Sachez qui a accédé aux données. Arrêtez qui ne devrait pas.
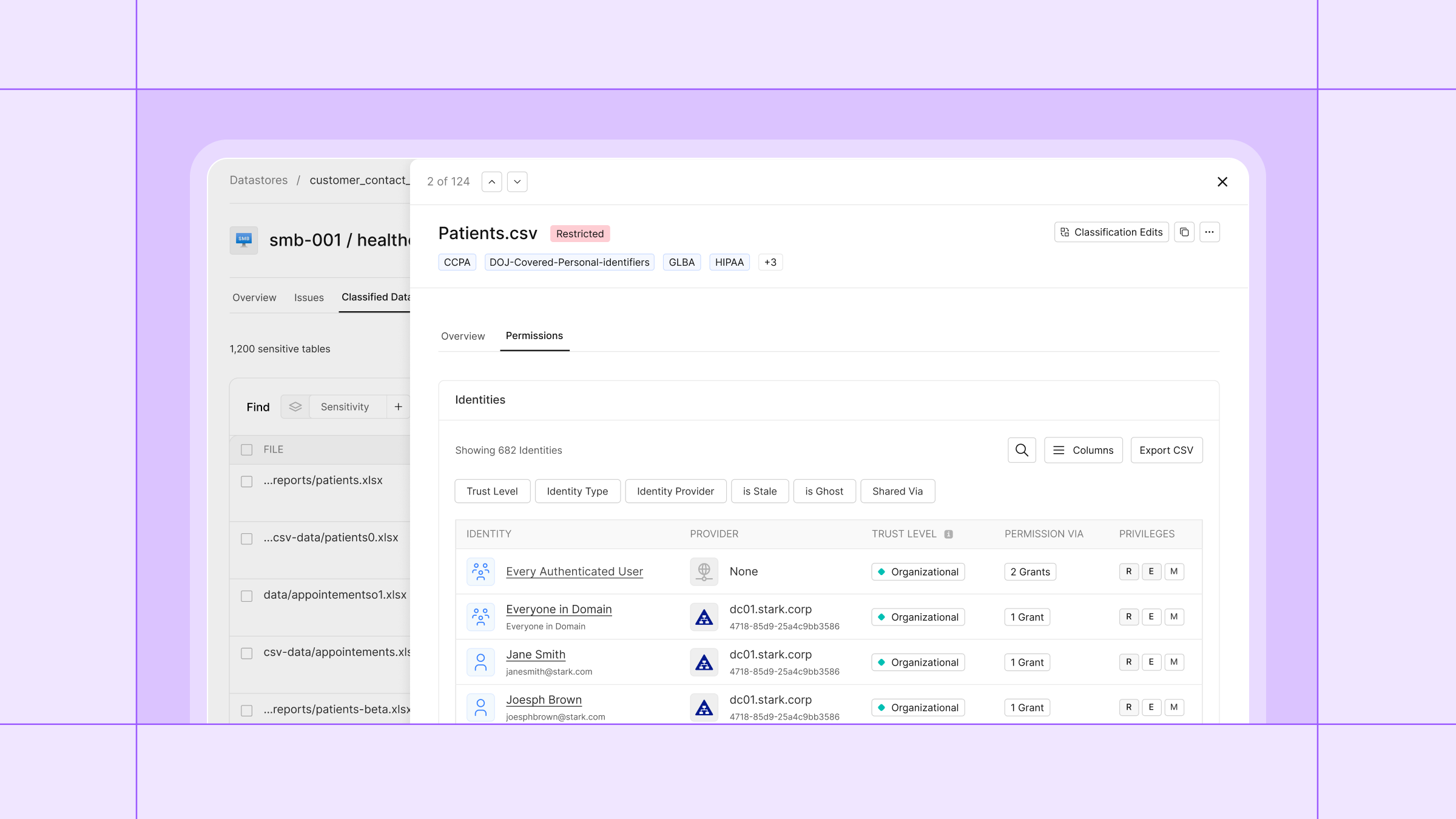
Sentier d'accès à Cyera résout ce problème en corrélant les données et le contexte d'identité avec l'activité d'accès. Cela crée un parcours d'activité vérifiable dans une vue facile à étudier. Et comme elle est basée sur la classification native de l'IA de Cyera, vous savez que l'activité n'est pas pleine de faux positifs. Vous pouvez voir exactement quelle action un utilisateur a effectuée sur des données sensibles, d'où et quand. Cela donne aux entreprises la visibilité et la confiance qu'elles recherchent depuis des années.
Access Trail est conçu pour gérer l'ampleur et la complexité des activités du personnel d'une entreprise sans frais opérationnels supplémentaires. La plateforme peut traiter des dizaines de millions d'événements par jour et stocke les enregistrements pendant un an par défaut.
Activité d'accès soutenue par une classification des données native de l'IA
Comme Access Trail repose sur notre moteur de classification des données natif de l'IA, il offre l'étendue et la précision qui font défaut aux outils existants, tout en restant léger et facile à déployer. La solution surveille l'activité en fonction de l'identité humaine et de l'IA, enrichissant chaque événement avec des informations contextuelles telles que l'identifiabilité des données, la résidence, le rôle du sujet, les réglementations pertinentes et les mesures de protection. Ce contexte aide les équipes à identifier les accès inappropriés, à évaluer l'impact sur l'activité et la conformité, et à hiérarchiser les mesures correctives au lieu de passer au peigne fin des journaux incomplets ou non pertinents.
Avec Access Trail, vous pouvez surveiller :
- Quelles identités ou entités ont interagi avec des données sensibles
- Quelles actions ils ont effectuées
- Quelles données étaient concernées
- Lorsque ces actions se sont produites, jusqu'à la seconde
Il en résulte une visibilité continue qui contribue à la fois à la sécurité des données, à l'identification des comportements suspects, à la réponse aux risques et à la conformité.
Accélérez la réponse aux risques
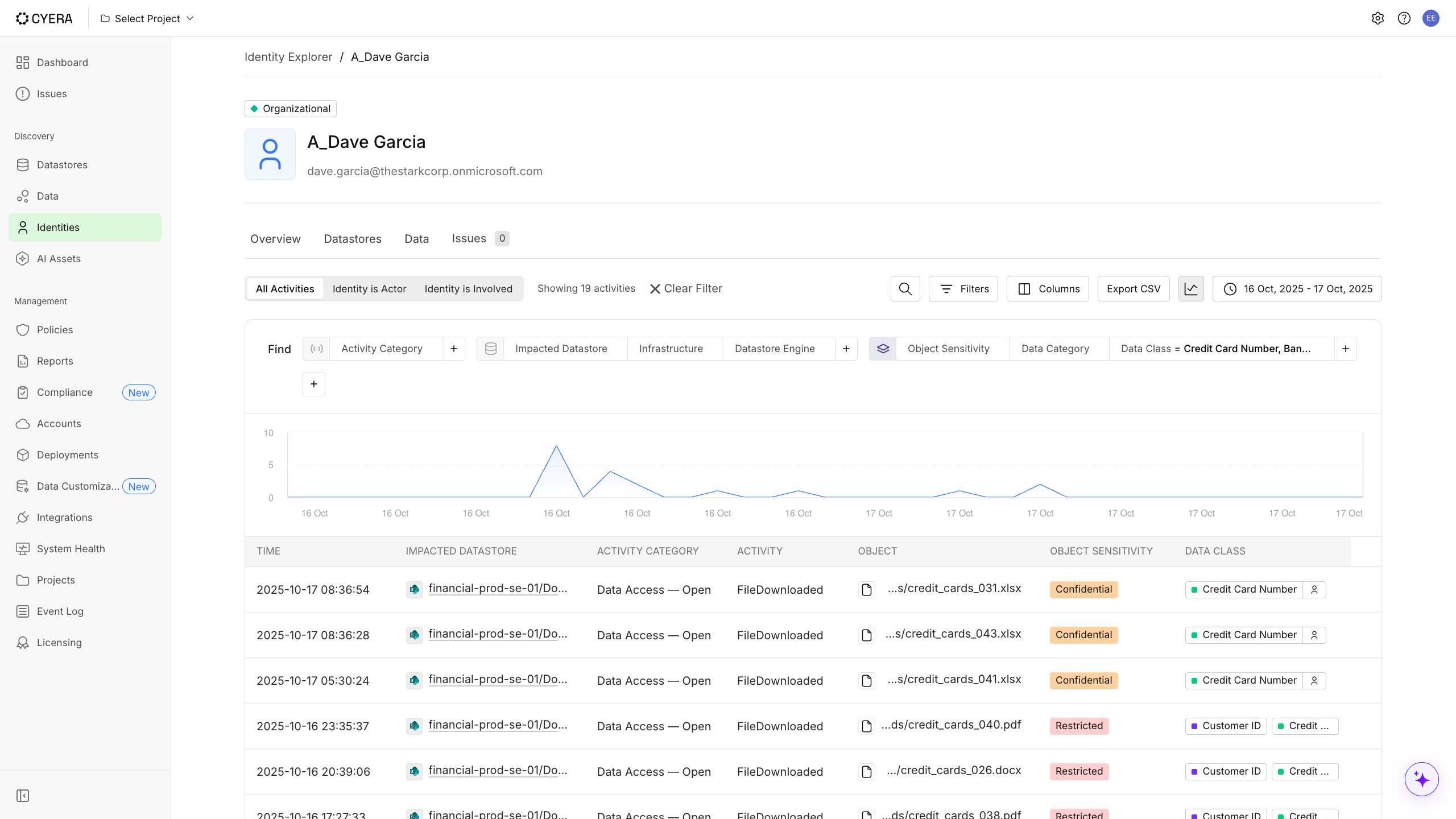
La rapidité est importante lorsque des données sensibles sont en danger. Access Trail permet à vos équipes chargées de la sécurité et des risques internes de comprendre clairement qui a agi, ce qu'il a fait et pourquoi c'est important en quelques secondes, et non en quelques heures.
- Enquêtez instantanément sur les activités internes : Révélez l'intention et le contexte qui sous-tendent les actions des utilisateurs grâce à des enregistrements d'accès précis et horodatés qui relient les données, l'identité et l'activité.
- Surveillez l'accès piloté par l'IA : Suivez la façon dont les outils et les agents d'IA interagissent avec les données pour enquêter sur les abus, empêcher l'IA parallèle et garder le contrôle des informations sensibles.
Renforcez votre posture en matière de sécurité des données
Access Trail vous permet de voir ce qui s'est déjà passé et d'en tirer des leçons, afin d'éviter que cela ne se reproduise. Grâce à ces informations, vous pouvez renforcer les défenses, combler les failles de sécurité et mettre en place une posture de sécurité des données plus résiliente au fil du temps.
- Clarifier la propriété des données : Confirmez la responsabilité des propriétaires de données afin de renforcer la gouvernance, d'améliorer la qualité et la sécurité des données et d'éliminer les ensembles de données orphelins ou non gérés.
- Appliquez le moindre privilège : Alignez en permanence les autorisations d'accès avec l'utilisation réelle pour empêcher la dérive des privilèges et réduire les risques.
- Minimisez votre empreinte de données : Trouvez et supprimez les données intactes et inutiles afin de limiter l'exposition, de réduire les coûts de stockage et de simplifier la gouvernance.
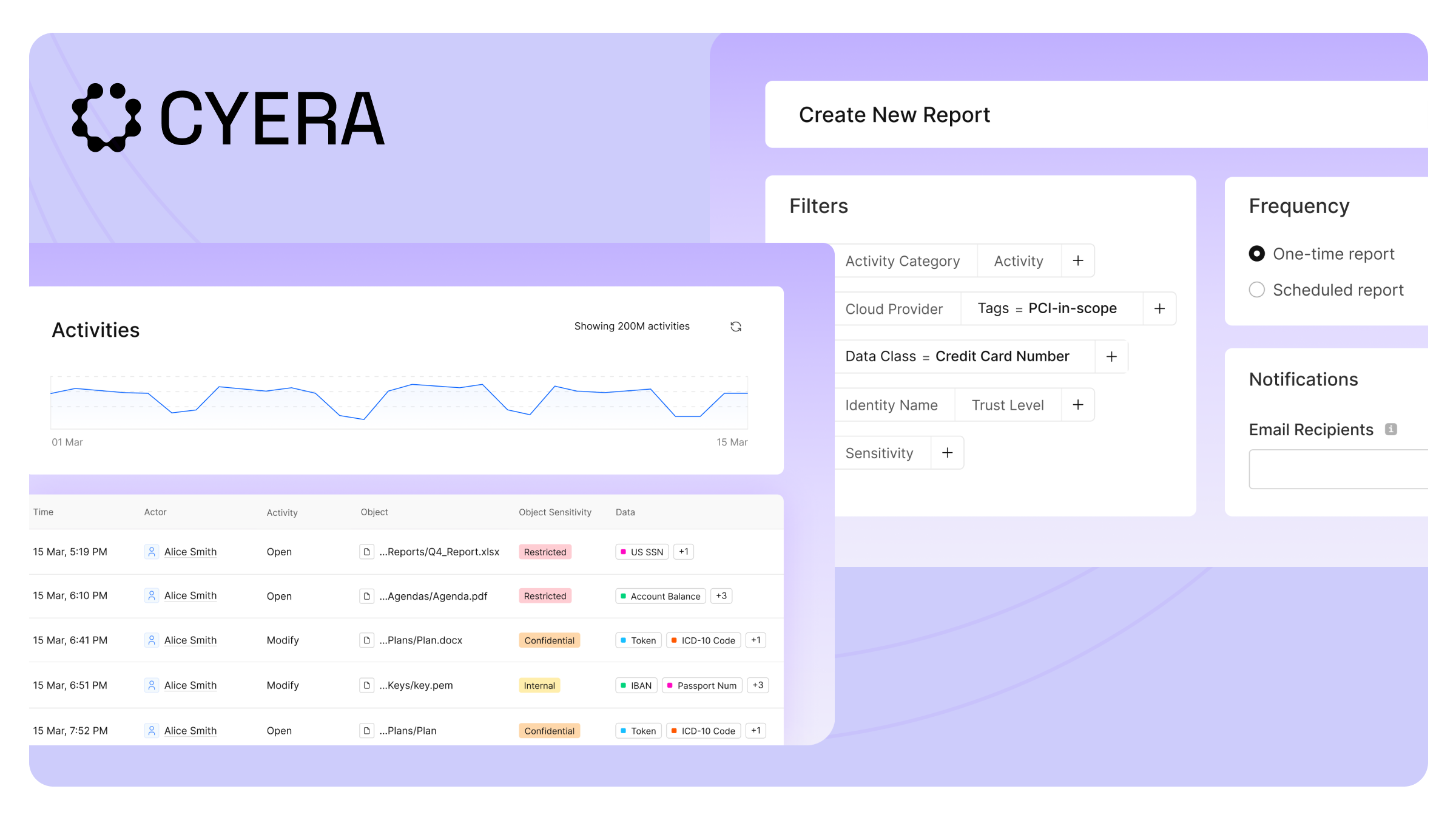
Simplifier et maintenir la conformité
La conformité doit valider votre contrôle, et non ralentir votre activité. Access Trail centralise et automatise la collecte de preuves afin que vos équipes puissent démontrer rapidement leur conformité et rester prêtes à tout moment.
- Générez des enregistrements de conformité en quelques secondes : Identifiez qui a accédé à des données sensibles, ce qui a été fait et à quel moment, le tout à partir d'une seule source vérifiable.
- Restez prêt à faire face aux audits en permanence : Bénéficiez d'une visibilité en temps quasi réel sur les activités d'accès et la sensibilité des données afin de pouvoir démontrer la conformité à tout moment, sans préparation manuelle.
L'avenir de l'intelligence d'accès
L'accès aux données est aujourd'hui complexe. Au fur et à mesure que les utilisateurs, les services et les agents d'IA interagissent avec des données sensibles, les organisations doivent savoir non seulement qui peut interagir avec ces données, mais également qui l'a réellement fait, ce qu'il a fait et pourquoi c'est important. Access Trail apporte cette clarté.
Êtes-vous prêt à voir Access Trail en action ? Demandez une démonstration si vous n'avez jamais exploré la plateforme Cyera. Pour les clients existants, contactez votre représentant Cyera pour en savoir plus.
Obtenez une visibilité complète
avec notre évaluation des risques liés aux données.