Understanding Who Can Access Sensitive On Prem Data with Cyera
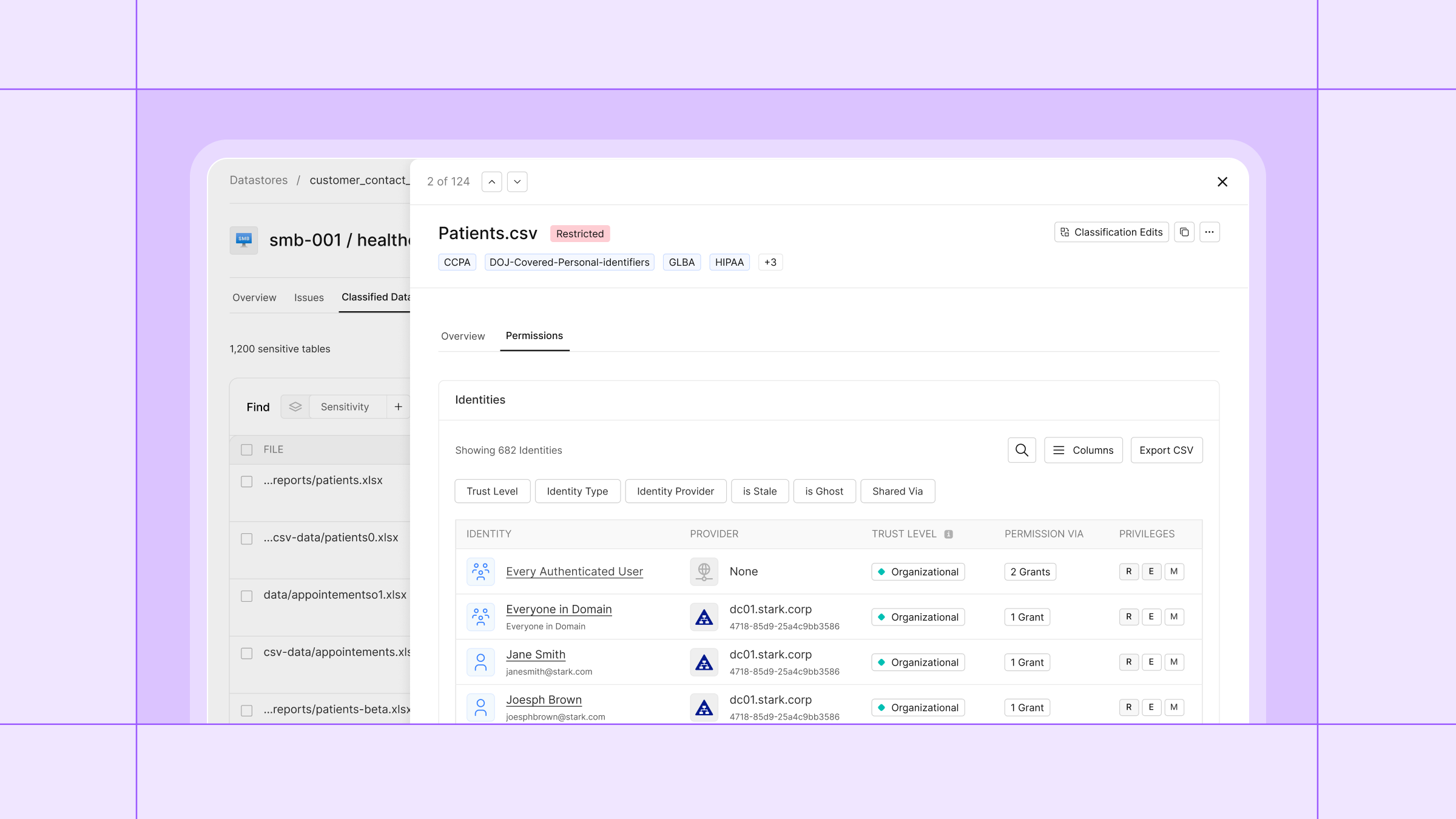
Who can access this file?
For most on-prem file shares, no one can answer that question with confidence. A single user may gain access through nested groups, inherited folder permissions, or legacy grants added years ago. Identity teams manage users and groups. Data security teams focus on sensitive files. On prem file shares sit uncomfortably in between, and the gap between identity and data is where risk quietly accumulates.
Most on prem file shares were designed to keep business moving, not to enforce least privilege. Over time, access expands. Groups grow. Permissions are copied forward. Folder inheritance is rarely revisited. Security teams know sensitive data lives in on-prem file shares like Windows SMB, NetApp, and Dell PowerScale, but understanding who can actually access it often requires manual lookups, scripts, directory searches, and assumptions no one fully trusts.
Cyera helps close this gap by connecting identity context with sensitive data in on-prem environments. Security teams can see who can access sensitive files, how that access is granted, and where permissions have quietly grown beyond what was intended.
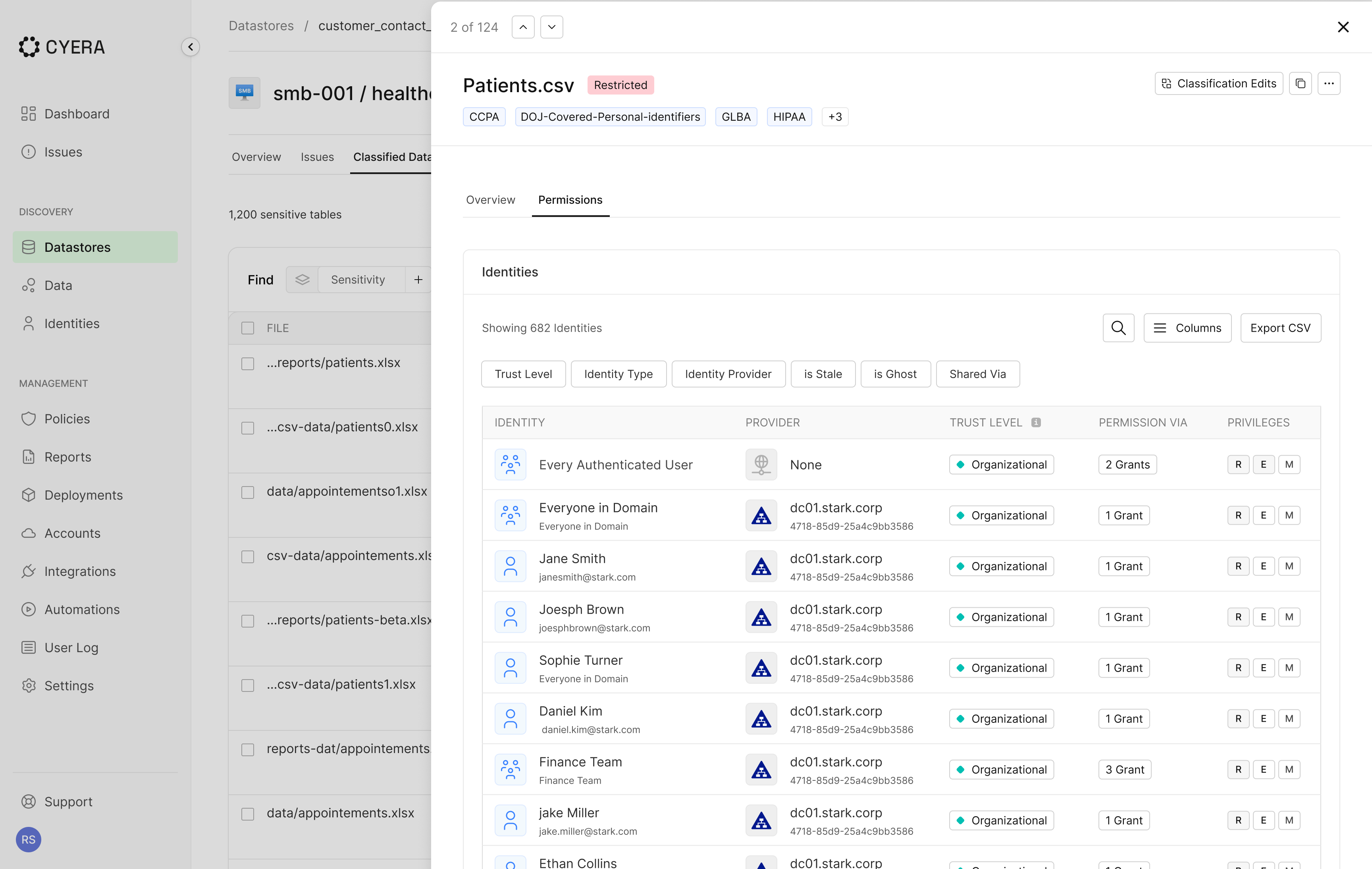
Why On-prem Access is Harder Than it Looks
On-prem file shares present a fundamentally different access challenge than modern SaaS platforms. There is rarely a single, reliable view of effective permissions. Instead, access is shaped by multiple overlapping layers:
- Group membership that is often deeply nested and poorly documented
- Folder and subfolder inheritance
- Domain and network wide permissions added for convenience
- Historical exceptions that outlived their original purpose
Each layer adds complexity. Together, they obscure reality.
A user may appear appropriately scoped on paper, yet still have access through a group buried several levels deep. A folder may look locked down, but inheritance quietly opens access to thousands of files below it. In long-running environments, where permissions are rarely removed, this complexity becomes a persistent source of exposure.
The Hidden Risk of Service Accounts
Service accounts often have some of the broadest access in on-prem environments and the least scrutiny. Created to support applications, backups, scripts, or integrations, these accounts are frequently granted wide permissions to ensure nothing breaks. Over time, they accumulate access across file shares, folders, and sensitive data types.
Unlike human users, service accounts are rarely reviewed as part of access certifications. They do not change roles, they do not leave the company, and they often bypass the controls applied to employee identities. In many cases, no one can clearly explain what data a service account can access or why it still needs that level of permission.
This creates significant risk. If a service account credential is compromised, an attacker may gain silent, persistent access to large volumes of sensitive data. Because activity often resembles normal application behavior, this access can go undetected for long periods of time.
Cyera makes this exposure visible by applying identity context to on-prem file shares. Teams can see which service accounts can access sensitive data, how that access is granted, and where permissions exceed what is necessary.
When Access Risk Becomes a Business Problem
Access blind spots are not just a technical issue. They directly impact compliance, audit readiness, and exposure management.
Regulations increasingly require organizations to demonstrate that access to sensitive data is appropriate, monitored, and limited to specific roles. Auditors ask clear questions:
- Who can access this data?
- Why do they have access?
- Is that access still justified?
In one on-prem environment, a scan revealed more than two million highly sensitive files spread across dozens of datastores that were accessible organization-wide. More than one billion records were effectively exposed. There was no breach. No alert fired. The risk existed simply because access had accumulated unchecked.
This is the type of exposure that often surfaces during an audit, an incident response investigation, or a board-level review, often before teams have clear answers.
Why Data Classification Changes The Access Conversation
Knowing who can access a file is only half the picture. The more important question is who can access sensitive data, and what kind of sensitive data it is.
Cyera combines effective access analysis with highly accurate, contextual data classification. It understands not just that data is sensitive, but why. Whether it relates to a customer, employee, patient, or vendor. Whether financial data is identifiable. Whether health data is regulated. Which compliance obligations may apply.
This context is critical in on-prem environments, where broad access is common and not all exposure carries the same risk. Accurate classification allows teams to focus on the small subset of files that contain the most sensitive data that pose the highest risk.
On-prem data presents challenges that legacy tools struggle to address. Unlike traditional tools that rely on regex or file location, Cyera’s learned classifications are inferred directly from unique data found within each customer’s environment, without training on similar data. This is especially important in on-prem environments, where organizations store proprietary formats, internal identifiers, and domain-specific data that legacy approaches often miss.
From Visibility to Access Governance
Access governance on-prem has historically been slow and manual. Without clear visibility, removing access feels risky, and teams often leave permissions untouched to avoid disrupting operations.
By showing effective access with full context, Cyera makes governance practical.Security and identity teams can identify high impact overexposure, such as org-wide access to sensitive data, and prioritize remediation where it matters most.
This supports least privilege without disrupting operations, and creates a defensible access model aligned to data sensitivity.
A Foundation For Compliance And Accountability
Access visibility is not just about reducing risk today. It establishes a foundation for ongoing compliance and accountability.
When auditors ask who can access sensitive data, teams can answer with clarity. When access reviews are required, teams can focus on real exposure, not theoretical permissions. When incidents occur, teams can quickly assess who could have accessed affected data and why.
Most importantly, access no longer lives in the shadows of legacy systems. It becomes visible, understandable, and manageable.
It’s Time to See On-prem Access Clearly
On-prem file shares are not going away. For many organizations, they remain home to some of the most sensitive and business-critical data.
Cyera’s Identity Module for On-Prem brings identity context, effective permission analysis, and data sensitivity together to help security teams uncover hidden exposure, enforce least privilege, and regain control over access risk across Windows SMB, NetApp, and Dell PowerScale environments.
If you cannot clearly explain who can access your on prem file shares, it is time to look closer. To see Cyera in action, request a demo today.
Obtenez une visibilité complète
avec notre évaluation des risques liés aux données.



