Data Risk Assessment (“DRA”) / Breach Readiness Assessment ("BRA")
Statement of Work (“SOW”)
This Statement of Work (“SOW”) is issued pursuant to, incorporates, is governed by the Master SaaS Agreement (the “AGREEMENT”) between Cyera and the Customer and sets forth the specific terms and conditions relating to the provision of Services referred to in this SOW. The combination of the terms of the SaaS License Agreement, the Order Form, and the provisions of this SOW shall together constitute the contract between the parties in respect of the Services. To the extent that there is a conflict between the SOW and the AGREEMENT, the AGREEMENT shall prevail. All capitalized terms not defined in this SOW shall have the meaning assigned to them in the Agreement.
1. Executive Summary
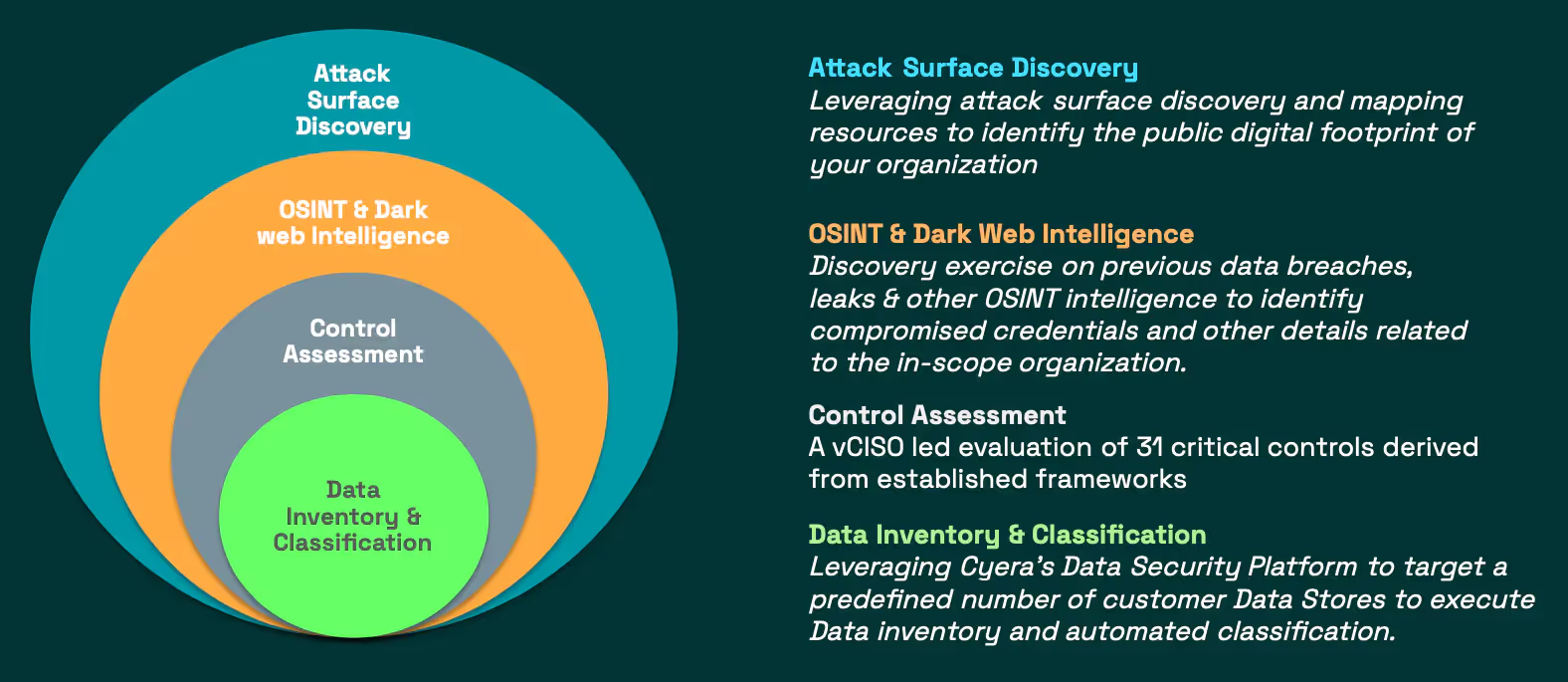
The Cyera DRA / BRA offers a comprehensive, engaging, and practical solution to assess your organization's data security and breach readiness practices. By leveraging 31 critical controls, Cyera's advanced data security platform, and intelligence from OSINT and Dark Web sources, we deliver actionable insights precisely tailored to your unique operating environment.
Cyera developed an innovative approach for discovering and classifying cloud data. The platform combines machine-learning, a passive, agentless architecture and guided remediation steps that:
- Deliver timely data classification and risk with an increased precision & recall
- Minimize effort to classify and contextualize data
- Continuously scan for changes to data classification and risk
- Deliver a unified classification, risk and remediation across SaaS, PaaS, IaaS for structured and unstructured data
As part of this SOW, Cyera will provide to Customer with its solution and supporting services to enhance cloud data security, governance, privacy, and risk management:
- Data discovery, classification & contextualization of structured and unstructured data
- Integrity validation for privacy and governance programs through the lens of sensitive data across cloud provider environments
- Provide the Customer with a summary of existing data repository attack surface
- Provide a digital footprint overview for the Customer in terms of external attack surface
- Provide the Customer with an summary of existing domain user compromised credentials and other exposed publicly available data
2. Detailed Approach
Control Review / Virtual CISO led evaluation of 31 critical controls derived from established frameworks (CIS, COBIT 2019, DAMA-DMBOK, ISO/IEC 27001, NIST SP 800-53, NIST CSF): Providing comprehensive coverage of data strategy and cybersecurity aspects relating to data.
31 Data Centric Controls leveraged:
- Data Governance Policy
- Data Stewardship Roles
- Data Strategy Alignment
- Data Classification and Tagging
- Regulatory Compliance Management
- Access Control Policies
- Data Quality Management
- Data Lifecycle Management
- Data Privacy Management
- Data Architecture and Design
- Data Integration and Interoperability
- Data Security Measures
- Security Awareness and Training
- Continuous Threat Monitoring and Intelligence
- Endpoint Security Management
- Master Data Management (MDM)
- Data Retention and Archival Policies
- Data Disposal Procedures
- Data Analytics Capability
- Data Literacy Programs
- Continuous Data Improvement
- Data Governance Committees
- Risk Assessment and Management
- Incident Response Planning
- Third-Party Data Management
- Key Performance Indicators (KPIs)
- Real-Time Data Monitoring
- Data Innovation and Adaptability
- Technical Vulnerability Management
- Incident Response Testing
- Mergers and Acquisitions Data Management
Control Review Input (example):
Control Review output (example):

Cyera Data Discovery & Classification exercise: Leveraging Cyera's Data Security Platform customers may target up to a predefined number of Data Stores and / or volume of data for discovery and classification.
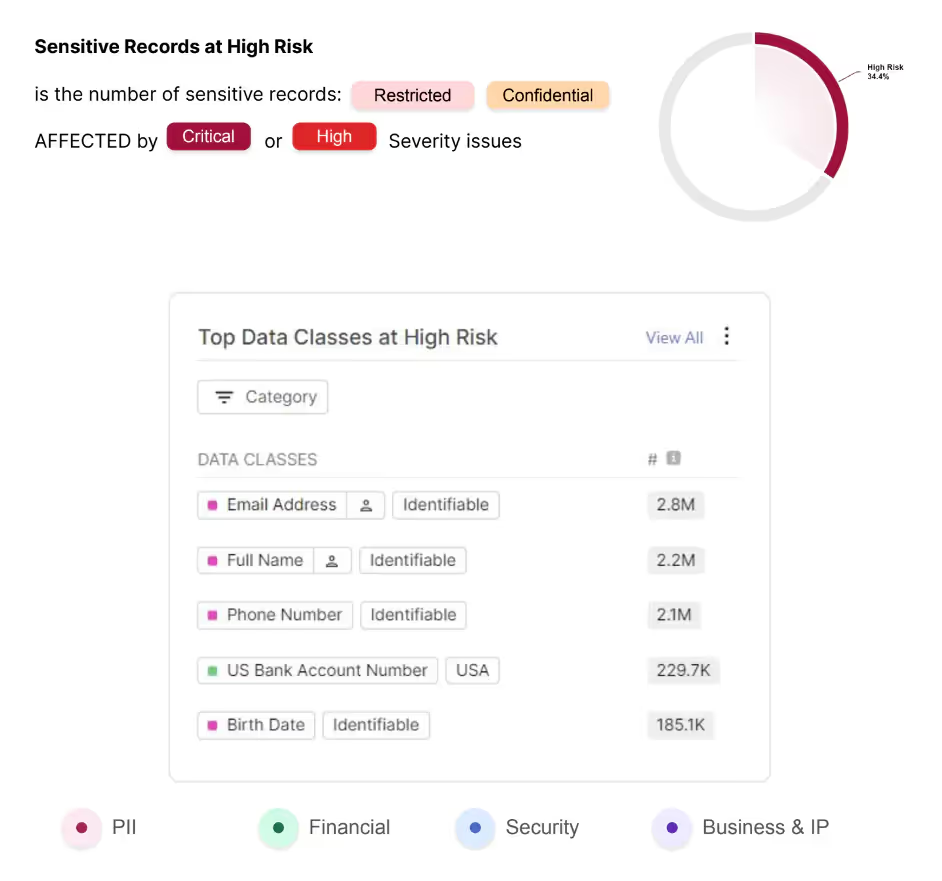
Data Discovery & Classification exercise output (example):
Breach Readiness / Table Tops:
- Breach preparation Table Top exercise activities led by vCISO resources:
- Example Table-Top Scenario 1: Data Privacy and Security Incident and Response
- Description: The CEO downloads the employee database to an Excel file and sends it unencrypted to HR, exposing sensitive data.
- Example Table-Top Scenario 2: Endpoint Security Breach and Response
- Description: A malicious actor exploits a vulnerability in an employee’s laptop to gain network access.
- Example Table-Top Scenario 1: Data Privacy and Security Incident and Response
Open source intelligence (OSINT) is the collection and analysis of data gathered from open sources (covert sources and publicly available information) to produce actionable intelligence.
Leveraging OSINT and Dark Web intelligence resources, perform a discovery exercise on previous data breaches and leaks to identify associated compromised credentials and other exposure details related to the in-scope organization.
External Attack Surface Discovery Exercise:
Attack Surface Discovery is an initial stage of reconnaissance that searches for publicly discoverable assets that belong to a particular organization. Cyera leverages industry standard approaches to identify the digital footprint of a given in-scope organization to identify all of the IT assets that are externally exposed to the internet. The purpose of this phase of the engagement is to highlight relevant cyber hygiene risks that could have a direct or indirect impact on data entrusted to the organization.
Data Risk Assessment Final Deliverable:
- Executive Summary: High-level overview of the assessment’s key findings and value.
- Detailed Findings: In-depth analysis of each control, highlighting areas of strength and improvement.
- Risk Assessment: Identification and analysis of key risks, with mitigation strategies.
- Recommendations: Actionable steps to enhance data strategy and cybersecurity maturity.
3. Scope
A. Prerequisites
To enable onboarding, Customer must provide the Cyera application access to the in-scope cloud environment(s). Customer is responsible for deploying the Cyera access roles and infrastructure (where applicable) in their in-scope cloud environment.
The scope of this Data Risk Assessment is limited to the following:
- 500 TB Data
- 3,000 SaaS Users
- Up to 2 domains / OSINT - Darkweb analysis
- Access to Cyera platform results for 30 days, post engagement.
B. Out of Scope Items
- External Penetration Testing activities
- External Vulnerability Assessment scanning
- Rescanning of scoped data repositories once successfully completed
C. Work Location
All work will be performed remotely.
D. Activities
Cyera performs the following activities to support Customer in onboarding and using the Cyera application. Many activities are sequential in nature and dependent upon completion of activities in the previous phase.
Cyera works with Customer to:
- Define meeting cadence and preferred communication channels
- Finalize technical deployment
- Onboard in-scope accounts in the Cyera application
Cyera:
- Conducts initial asset inventory scan of in-scope cloud environment
- Leads initial user training session
- Conducts OSINT exercise
- Conducts External Attack Surface Exercise
- Perform interviews / question - answer sessions with Customer representation.
Outcome: Initial Asset Inventory (Cyera Platform), Control mapping and Q&A completed
E. Timeline:
The duration of each phase is based on Cyera's best estimates, drawing from our extensive experience with similar implementations. Depending on the Customer's specific requirements and level of involvement, Cyera may be able to deliver priority scans and services outlined above ahead of schedule.
4. Proposal
A. Customer Obligations
- Customer is obligated to provide the Cyera application required access to the in-scope cloud environment(s).
- Customer is obligated to provide the necessary resources such as data, equipment to support onboarding.
- Customer is obligated to have internal personnel available to Cyera resources over the life of the engagement for interviews, clarification, etc.
B. Assumptions and Dependencies
The project, quote and estimated timelines are based on the following key assumptions. Parties agree that any changes in the assumptions may result in an adjustment in the quote, project scope, or estimated delivery timelines.
- Cyera and Customer will agree upon cloud accounts and assets (“accounts”) for onboarding and scanning. In-scope accounts will adhere to Customer’s Cyera licenses and be documented in the shared “Success Plan” document.
- Customer will not modify the default Cyera platform deployment scripts (e.g., removing or qualifying permissions).
- The Cyera platform is compatible with Customer’s cloud environment including but not limited to the Customer software and infrastructure licenses, configurations, and versions. Cyera will make commercially reasonable efforts to resolve incompatibility issues.
- Third-party software or services required for the project will be available and accessible to the Cyera team.
- Any changes to the scope of the project will require a change request, and any additional work or expenses outside of the scope will require an additional agreement and may result in additional fees.
- Any customization requests made by Customer are feasible within the scope of the project and Cyera’s capabilities and will not significantly impact the project timeline or budget.
- Cyera is not responsible for any unauthorized access to customer assets during or post engagement.
- Cyera is not responsible for any data source outage as part of this engagement.