Streamlining Data Security Policy Management with Cyera
.avif)
Security teams don’t have enough hours in the day, which is why it’s critical to focus on high-impact work. But with so many competing priorities, it can be difficult to determine which data security use cases need solving first. We built the Policy Catalog to alleviate this pain, helping data security leaders prioritize what matters most.
The catalog centralizes critical use cases into a single dashboard, giving you the chance to pick and choose the policies and controls that align with your needs. By organizing the catalog around use cases, we’ve created a more intuitive way to enforce data security at scale.
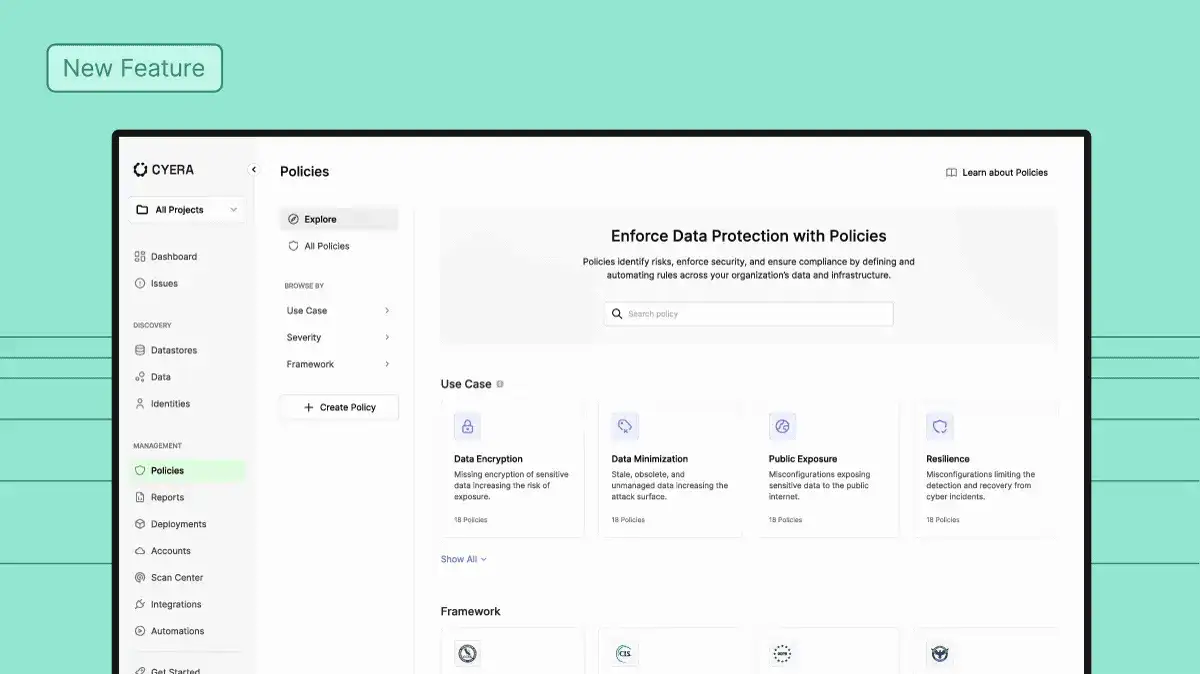
A More Intuitive Policy Experience
Security teams can now easily find, filter, and apply policies based on use case, severity, and compliance framework. Policies can be enabled with a single click or through bulk activation for faster, more consistent enforcement across environments.
Policies Aligned with Real-World Risks
Security policies often feel disconnected from actual threats. We’ve refocused policies around practical use cases that directly impact data protection and compliance. By structuring policies around real business needs, security teams can drive meaningful and measurable outcomes.
Uses cases covered, include:
- Data Sprawl: Uncontrolled sprawl of sensitive data across systems and clouds
- Mislabeled Data: Incorrectly labeled data reducing the effectiveness of security controls
- Resilience: Misconfigurations limiting the detection and recovery from cyber incidents
- Third-Party Access: Sensitive data accessible by external parties
- Public Exposure: Misconfigurations exposing sensitive data to the public internet
- Organizational Access: Overpermissive access to sensitive data within an organization
- Data Minimization: Stale, obsolete, and unmanaged data increasing the attack surface.
- Data Encryption: Missing encryption of sensitive data increasing the risk of exposure
Smarter, More Focused Policy Activation
Out-of-the-box policies can be overwhelming, especially when there is little guidance on where to start. We’ve eliminated the guesswork with automated policy activation. New customers get a clean, prioritized starting point with only high and critical policies enabled for the datastores they actually use.
As new datastores are added, only the most relevant policies are automatically activated, keeping the policy catalog lean and focused.
This approach reduces noise and clutter, helping security teams zero in on what matters most without unnecessary configuration overhead.
A More Strategic Approach to Policy Management
Implementing security policies can still be complex, but finding the right ones shouldn’t be.
Cyera’s Policy Catalog makes it easier to browse, filter, and understand available policies based on real-world use cases. It’s a step toward simpler, more manageable policy workflows. To summarize, with Cyera’s Policy Catalog, you can:
- Find and manage policies faster with an intuitive interface.
- Align policies with business needs through practical use cases.
- Enforce policies efficiently with one-click bulk activation.
Request a demo to explore the Policy Catalog today.
Gain full visibility
with our Data Risk Assessment.



