Uncover Who’s Behind the Risk: Cyera Now Surfaces the Identities Behind Every Data Security Issue
Cyera now shows exactly who caused each issue, so you can stop guessing and start fixing faster.
When security teams see a data exposure issue, the first question is usually: “Who can actually access this?”
Whether it’s a sensitive file in Microsoft 365 or an S3 bucket exposed to external accounts, understanding which identities have access is key to assessing risk and determining how to fix it.
Cyera’s new Offending Identities feature helps you answer that question fast, with clear evidence of who caused an issue to trigger and how much access they really have.
Why Identity Context Is Key to Reducing Data Risk
Most data security issues don’t stop at the object - they start with access. If you don’t know who has access to sensitive data, you don’t know the real risk.
A full 57% of security teams say overprivileged access is their number one data risk, and nearly one-third admit they can’t confidently track which identities have access to sensitive data[2].
That’s where Cyera’s Identity Module comes in. It brings together access and data context to uncover how human and machine identities expose your data, whether it’s through stale roles, unknown vendors, or AI tools like copilots.
And this matters more than ever. Gartner reports machine identities are now the fastest-growing identity type in the enterprise, but the least governed[1]. Cyera gives you visibility into those, too.
Already using Cyera to detect exposure? The Identity Module helps you reduce it by showing exactly who has access and whether they should. Offending Identities takes it a step further by showing who triggered the risk and what to do about it.
Here’s the reality: only 13% of organizations feel truly confident in their ability to detect and respond to data security and privacy exposures[2].
And because it’s fully integrated into your DSPM workflows, it simplifies audits, supports faster investigations, and keeps your access policies tight without slowing the business down.
Know What’s Exposed, but More Importantly, Who’s Behind It
Most data security tools show what is exposed. Cyera goes a step further by showing who is behind it.
The new Offending Identities tab in the Issue Details page reveals the exact users or accounts responsible for triggering an issue. This includes:
- Personal email addresses with access to confidential corporate files
- External AWS accounts accessible to your production buckets
- Overexposed Microsoft 365 groups, including nested and dynamic groups
- Inactive roles or identities without recent activity, retaining sensitive access
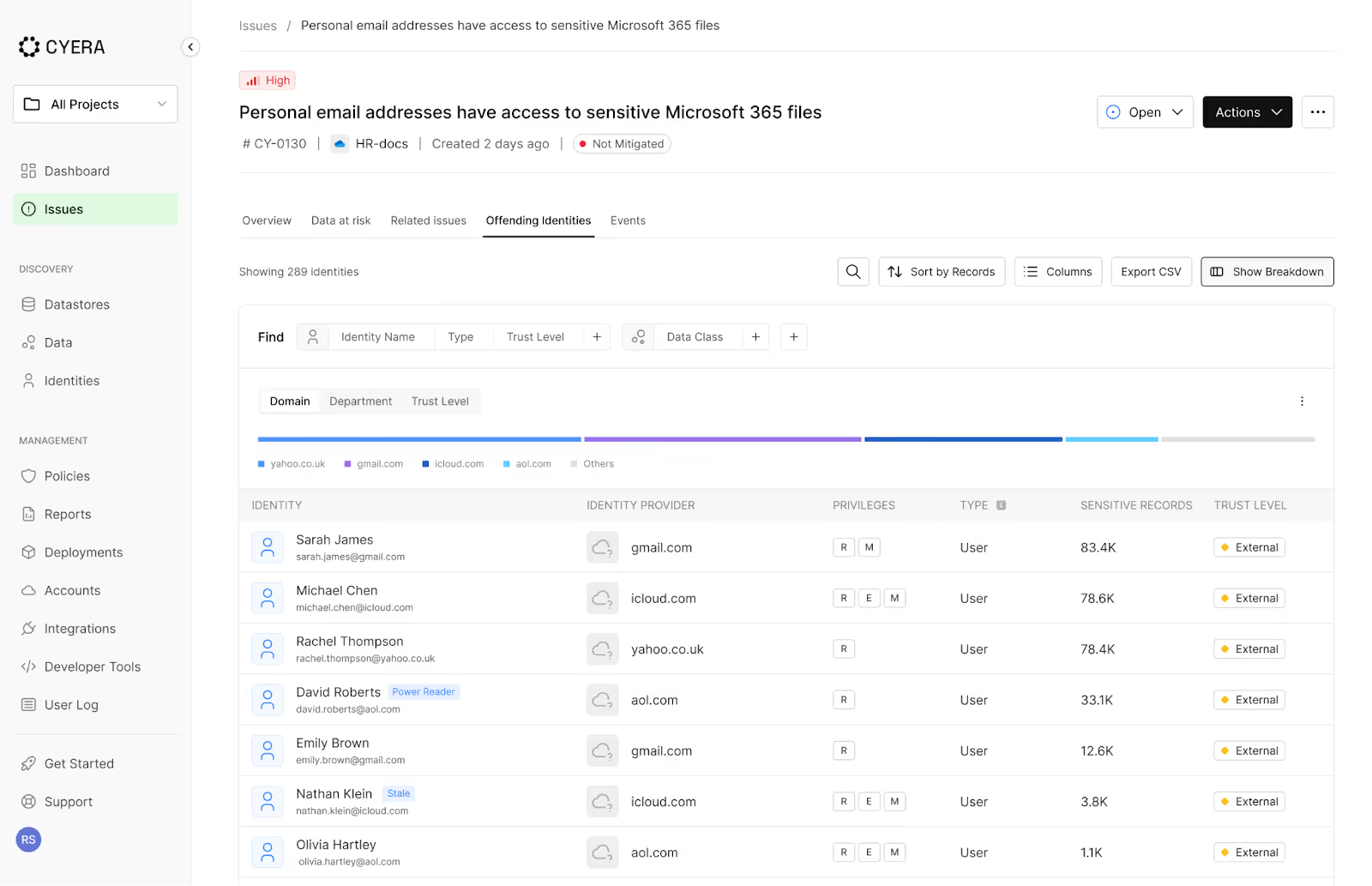
This level of clarity lets you triage faster and remediate smarter. Instead of spending valuable time investigating the cause of an exposure, your team can immediately understand the source and focus on fixing it. That means prioritizing remediation efforts more accurately and taking direct action on the identities responsible.
Understand Identity Risk in Context
Not every identity poses the same risk. What matters is how much sensitive data they can access and their security posture. Cyera now adds rich context next to each offending identity—how much sensitive data they can access, how recently they were active, their MFA enforcement status, last password rotation date, group size, and even organizational details like department and job title. With this insight, teams can focus on the identities that pose the greatest risk and act quickly to mitigate them.
Go the Other Way: Identity-Centric Risk Views
Need to investigate a specific user or account?
In addition to showing which identities triggered an issue, Cyera now also enables teams to start from the identity itself. The new Issues tab in the Identity Details page provides a consolidated view of every data security issue linked to a specific user or account.
This is invaluable for:
- Investigating insider risk cases
- Reviewing highly-privileged service accounts
- Assessing third-party vendors’ permissions
You don’t just see what someone can access - you see what problems they are causing.
Example Scenarios
- Personal Emails with access to sensitive Microsoft 365 Files: Granting access to personal emails creates security risks, including unintended access by current and former employees. Cyera flags gmail.com users with access to sensitive Microsoft 365 files, so you can quickly identify which are approved contractors and which represent unauthorized access.
- Internal Overexposure via Dynamic Groups: Large dynamic Microsoft 365 groups can unintentionally provide thousands of users access to sensitive documents. Cyera reveals the group and its members, so you can assess if the group should retain access or be restructured.
- Eliminating Stale Access Risk: Inactive AWS IAM roles with access to sensitive S3 buckets are a common blind spot that violate the least privilege principle. Cyera detects these stale identities, helping you remove access before it can be exploited, reducing your attack surface
From Visibility to Action, Faster
These identity insights are not just additional context. They’re the missing link between detection and remediation. With Cyera:
- You know who caused the problem
- You understand their level of risk
- You can take direct remediation steps
This is how teams cut through noise and reduce real exposure, resolving issues with speed and confidence.
See who’s putting your data at risk and take action today. Request a demo.
[1] Gartner, Innovation Insight: Improve Security With Machine Identity and Access Management, 2025
[2] Cyera, 2024 DSPM Adoption Report: Data Security Trends and Challenges, 2024
Gain full visibility
with our Data Risk Assessment.



